-
Content Count
19,189 -
Joined
-
Last visited
Never -
Feedback
N/A
Posts posted by Rss Bot
-
-
The idea of a music video is to generate promotion; to give extra air time to an artist in front of a chosen demographic, with the aim of increasing awareness and sales.
The MTV Generation saw the creation of numerous animated videos, but as technology became more accessible and the platforms available for showing media grew, the possibilities for animation in music videos increased.
The list below has been compiled to show a broad range of the animated music videos that are out there. Not all of them are strictly 'animation' (in the cartoon sense); some are motion graphics, 3D, lo-fi, hand-drawn and so on. And they're in no particular order...
01. Taylor Swift - Look What You Made Me Do (Lyric Video)
- Released: 2017
- Directed by: ODD
Taylor Swift marked the start of her musical return with this animated video created by ODD. Featuring images of snakes that have been popping up on Swift's recently cleansed social media profiles, this video continues the long tradition of listeners indulging in rampant speculation as to who the pop phenomenon is referring to.
Interestingly, the official title of this animation points out that it's a lyric video. This of course makes sense when you watch it and see each syllable of Swift's lyrics spelled out on screen, but it makes us wonder if there's a more traditional, non-animated video on the way for this song, possibly to tie in with an official album launch.
02. The Killers – Miss Atomic Bomb
- Released: 2012
- Directed by: Warren Fu
Director Warren Fu had previously worked with the band on their video for single Runaways, and returned to take charge of this, their second single. Effortlessly fusing the media of animation and stunning live action shots, this animated music video brings a heartbreaking love story to life.
Josh Goldstein worked as the producer, with Jeff Pantaleo as executive producer and Shawn Kim as director of photography. Titmouse Studio was responsible for the exceptional animation.
03. Tame Impala – Feels Like We Only Go Backwards
- Released: 2012
- Directed by: Becky Sloan, Joseph Pelling
You could say that the inspiration for this animated music video lies somewhere between Peter Gabriel's Sledgehammer and The White Stripes' Seven Nation Army. The amount of work that's clearly gone into it makes it a true work of art.
Directors Becky Sloan and Joseph Pelling have a creative chemistry that always produces the best results, whether it's applied to set design, window displays, Christmas cards or TV idents. Feels Like We Only Go Backwards is an absolute delight.
04. Home and Dry – Ghosts Are Dancing
- Released: 2012
- Directed by: Maxime Causeret and Gilles Deschaud
This video for Parisian art-rock band Home and Dry is a personal project made mostly using Houdini. The dramatic effect was created by filming a motion capture of the band's lead singer Laure Laffererie's face with two cameras. The effect was then created in 2D using motion vector and 3D lighting.
Sadly it doesn't look like the band have put out new music since 2012, but we think this video is still worth a watch.
05. Steven Wilson – The Raven That Refused To Sing
- Released: 2013
- Directed by: Jessica Cope and Simon Cartright
Clearly inspired by the work of Russian animator Yuriy Norshteyn (best known for the incredible Tale of Tales) the intense atmosphere of this imaginative and thought-provoking short brings the haunting story of the song to evocative life. The stark and simplistic animation style – based largely on the gentle movements of hand-cut paper models – fits the mood perfectly.
06. The Kleenrz – Sandman
- Released: 2012
- Directed by: Jason Brown and Aya Yamasaki
Combining children's television-style cartoon characters with live action, this music video follows the Sandman as he works with his two helper umbrella girls, and reveals what goes on inside the big bag he carries. The action cleverly synchronises with lyrics by The Kleenrz, a collaboration by LA rappers Self Jupiter and Kenny.
The beauty of this approach is that it gets you to listen carefully to the lyrics. This is something that can be difficult to achieve with music videos, as often the action distracts from the song itself.
07. Smashing Pumpkins – Tonight, Tonight
- Released: 1996
- Directed by: Jonathan Dayton and Valerie Faris
US husband and wife duo Jonathan Dayton and Valerie Faris have directed music videos for the likes of R.E.M. and Paula Abdul, as well as Little Miss Sunshine. They paid homage to silent film director Georges Méliès' A Trip to the Moon for this animated video. To me, this is possibly one of the greatest music videos ever made.
08. Daft Punk – One More Time
- Released: 2000
- Directed by: Kazuhisa Takenouchi
The 2003 anime film Interstella 5555: The 5tory of the 5ecret 5tar 5ystem, also directed by Kazuhisa Takenouchi, would be a continuation of the stories told in Daft Punk videos One More Time; Aerodynamic; Digital Love; and Harder, Better, Faster, Stronger.
09. Queens of the Stone Age – Go With The Flow
- Released: 2003
- Directed by: Shynola
Shynola are a four-piece collective who have worked with the likes of Beck, Radiohead and Blur, while also producing animation sequences for The IT Crowd and Scott Pilgrim Vs The World.
10. The Cribs – Mirror Kissers
- Released: 2006
- Produced by: Diamond Dogs
UK music video directors Diamond Dogs (Olly Williams and Philip Sansom) have directed for the likes of The Hoosiers, Jack Peñate and Maximo Park, and have a very distinct style. The video for Mirror Kissers was shot on a plain white background, then around 2,740 frames were printed, photocopied and manipulated before being edited back together to produce this fascinating video.
The concept works very well – it's stylistically spot on. It's not your typical music video as it's laced with blemishes and is rather ugly, all of which actually compliments the track it's supporting.
11. Gorillaz – El Mañana
- Released: 2006
- Directed by: Pete Candeland
Pete Candeland boast a huge repertoire of well-known pieces: the BBC's 2008 and 2012 Olympic marketing campaign, the Beatle's RockBand promos, plus numerous music videos for Gorillaz. You couldn't compile a list of animated music videos and not include Gorillaz, a band that was seemingly created for this format.
12. Los Campesinos! – We Throw Parties, You Throw Knives'/'You, Me, Dancing!
- Released: 2007
- Produced by: Monkmus
American animator Monkmus has created an array of music videos for the likes of Badly Drawn Boy, Mogwai and Death Cab for Cutie. This double effort for Los Campesinos! stood out the most for me as I love the contrasts and similarities between war and party. The naive style of the illustration is beautiful and reminds me of the tail end of the infamous Dumbo scene with the racing elephants.
13. MGMT – Time To Pretend
- Released: 2008
- Directed by: Ray Tintori
American Director Ray Tintori has directed music videos for The Cool Kids and The Killers, as well as MGMT. I love the lo-fi and slightly dystopian look of this video. It's unpolished and very raw around the edges, but also has a very warm psychedelic quality.
14. London Grammar – Hey Now
- Released: 2014
- Directed by: Chris Ullens
Chris Ullen's stunningly atmospheric video for London Grammar's Hey Now perfectly reflects the song. For this work Ullen collaborated with string artist Sebastien Preschoux.
In the video, balls of string and light dance amongst trees as a forest comes alive in a night time setting.
15. REM – Man Sized Wreath
- Released: 2008
- Directed by: CRUSH inc.
Toronto-based CRUSH inc. teamed up with REM to produce this very effective effort. CRUSH inc. have notably worked with IKEA, Budweiser and Nintendo.
I'm really intrigued by the many different styles in this video – from low-fi techniques, to 3D modelling via pixelated video games graphics. Normally, this really wouldn't work well together – but strangely enough, here it really does.
Next page: Basement Jaxx, Coldplay, The Shins, and more!
16. Basement Jaxx – My Turn
- Released: 2009
- Produced by: Tomek Ducki
Tomak Ducki is an animator and designer based in Krakow, Poland. He's had numerous festival screenings and won awards for his distinct style of work. I really appreciate the minimal style of this video; the colours work so well together and give it quite a mystical vibe.
17. Everything Everything – Schoolin'
- Released: 2010
- Directed by: Nicos Livesey
London-based freelance illustrator and animator Nicos Livesey produced this fascinating minimalist music video for Everything Everything. I really like the style and pace of this video, and how it tries to capture as many of the lyrics as possible, with brightly coloured, but minimal imagery.
18. Sebastien Tellier – Look
- Released: 2010
- Directed by: Mrzyk & Moriceau
This wonderfully creative music video for Sebastien Tellier follows around a female bottom for the duration, but shows the evolution and devolution of everything around her, from clothing, to grass and her skeleton. For a simple outline animation, it's very captivating. Mrzyk & Moriceau's style of capturing a journey is also visible in their video for Air's Sing Sang Sung.
19. Coldplay – Always in my Head
- Released: 2014
- Directed by: Alasdair+Jock
Animation duo Alasdair + Jock created the animation for a full 43-minute stream of Coldplay's sixth studio album, Ghost Stories.
They used Mila Fürstová's beautiful album artwork – etched angel wings over an ocean – as the basis for their video, and brought it to life using a combination of 3D, 2D cutouts and 2D drawings. A total of 50 individual sections were created before being edited to ensure the line style of the animation exactly replicated that of the album artwork. The result is mesmerising.
20. The Maccabees – No Kind Words
- Released: 2009
- Directed by: Alexander Brown and Orlando Weeks
This video features actors Mathew Horne (of Gavin & Stacey fame) and Matthew Baynton (who also starred in the comedy series) in what reminds me of an Alas Smith and Jones conversation piece, laced with pixelated video game visuals – before the camera swings round to a front-on of Mat Horne, complete with neon green visuals tracing his face.
Brown has also worked on music videos for James Blake, and Gabrielle Aplin's The Power of Love.
21. Is Tropical – The Greeks
- Released: 2011
- Produced by: Seven
This animated music video went on to win at the 2011 UKMVA's for Best Indie/Rock Video – UK and Best Animation in a Video. It's a perfect blend of live action footage of children playing with toy guns, plus animation bringing the guns to life, in a dark-yet-naive video.
22. TOY – Lose My Way
- Released: 2012
- Produced by: Brass Moustache
Brass Moustache is an independent film collective based in London. Individually, they are musicians, photographers, illustrators and journalists. This effort for TOY is simply done, but extremely effective – a wide one-shot performance overlaid with a beat-matched psych particle system and sections of the singer/guitarist performing.
23. House Shoes ft. Danny Brown – Sweet
- Released: 2012
- Directed by: RUFFMERCY
Russ Murphy/RUFFMERCY has animated and produced numerous videos for the likes of Paul Weller, as well as live loops for Ministry of Sound.
RUFFMERCY has a very interesting visual style. This video in particular boasts a trippy flow of melting faces.
24. The Shins – Rifles Spiral
- Released: 2012
- Directed by: Jamie Caliri
Jamie Caliri is a Grammy-nominated director who created this very eerie-looking music video for The Shins. The video follows a battle between magicians and a rabbit. I love the aesthetic of this. It's very unpolished and rather Tim Burton-esque, and really nicely blends 2D and 3D elements.
25. Silvery – Horrors
- Released: 2008
- Produced by: Alasdair + Jock
Alasdair + Jock met at Edinburgh College of Art and have gone on to produce numerous music videos, win multiple awards and produce sections for 3D feature, A Liar's Autobiography, by Graham Chapman (of Monty Python fame). I love the flow of this video. The simplicity of the moments and the intensity of the aesthetics really go well to compliment each other and the track itself.
Next page: the videos that didn't quite make the cut!
HONOURABLE MENTIONS (or ones that are in most lists...)
Dire Straits – Money For Nothing
- Released: 1987
- Directed by: Steve Barron
Peter Gabriel – Sledgehammer
- Released: 1986
- Directed by: Stephen R Johnson
Radiohead – Paranoid Android
- Released: 2007
- Directed by: Magnus Carlsson
Blur – Coffee & TV
- Released: 1999
- Directed by: Hammer & Tongs
White Stripes – Fell In Love With a Girl
- Released: 2002
- Directed by: Michel Gondry
Jack Beats – Careless
- Released: 2012
- Directed by: Rob+Rob
Also read:
-
An obscure Apple kernel extension patched in iOS 10.3.3 was originally built without security measures in place, according to the researcher who privately disclosed the flaws.
-
Getting your business card right is perhaps the ultimate test of your typographic skills. With only a small amount of space, it’s a challenge to create something fresh, original and distinctive while still including all the practical information you need to convey.
Here we bring you nine business card designs by type and lettering designers that creatives of all stripes can learn from.
01. Jessica Hische
Hische’s business cards put a smile on people’s faces at Adobe Max
Jessica Hische is a typographer and illustrator working in San Francisco and Brooklyn. Actively involved in the type community (she served on the Type Directors Club board from 2012 to 2015), her clients so far have included Wes Anderson, The United States Postal Service, Tiffany & Co, The New York Times, Penguin Books, Target, Starbucks, American Express, and Wired Magazine.
Hische ordered these ‘quickie’ business cards online from Moo’s Luxe line so she could hand them out at the Adobe Max event in LA. It just goes to show that you don’t need to pay for expensive finishes to make an impact. A dash of wit, a utilitarian design and a clear, legible font can be far more effective.
02. Happy Letters
The delight is in the detail with this agency’s letterpress cards
Happy Letters is a lettering, calligraphy and graphic design studio based in Madrid. And it announces itself in style with these sumptuous, blind-pressed business cards. The textured white background combines a variety of typographic and illustrative styles that say ‘hello’ in a number of different languages. It’s a lovely touch that you may not even notice at first, but it leaves a positive lasting impression.
03. Adam G
Gonzalez’s monochrome business cards are beautiful in their simplicity
Adam Gonzalez is a full-time designer with a strong focus on typography and illustration. Based in Los Angeles, his skills include hand lettering and sign painting. These lovely letterpress printed business cards show just how simple a design can be, while still effortlessly communicating the skills and artistic judgement of its maker.
04. Sean Tulgetske
Tulgetske’s business cards combine the best of vintage and modern style
Sean Tulgetske is a freelance designer based in Michigan. With clients including ESPN, Disney, Pixar, VH1, Target, Southwest Airlines and Nike, his work is strongly focused on hand lettering, type design and illustration. We love the hand-stamped effect used in his business cards, which helps the design evoke both a sense of the retro and a feeling of modernity.
05. Sean McCabe
McCabe’s letterpress cards draw on the power of minimalism
Sean McCabe is a hand lettering artist from San Antonio, Texas, who also runs online training courses and podcasts under the monicker Seanwes. These letterpress cards harness the power of minimalism and white space, conveying his skills far more powerfully than something busy and flashy might have done.
06. Studio Moross
These multicoloured business cards suggest, rather than reproduce, Moross's characteristic lettering designs
Studio Moross is the creative home of Kate Moross, a London-based art director best known for her colourful, freeform lettering designs. Rather than simply reproduce her crazy letterforms – which might prove a little complex and overpowering for a business card – these cards represent her style in a subtler fashion, through their multiple, bright hues and the artful squiggle running across them.
07. Branding with Type
Romanos puts his own fonts front and centre on his business cardsAlberto Romanos is founder and type designer of Branding With Type, a Spanish studio that designs bespoke fonts for brands. As such, he needed the type on his business cards (the company’s own Quinta, and Flat Sans for Flat 101) to be front and centre. Then he added a big splash of neon yellow, and put it all through silkscreen and letterpress printing processes. That might sound a bit nuts, but the result is pretty sophisticated, as you can see.
08. Andrew Wolfenden
Wolfenden makes white-on-black type work well in these cleverly designed cardsAndrew Wolfenden is a freelance graphic artist and designer from Liverpool based in Road Studios who puts a strong focus on typography in his work. Putting small white type on a black background means entering a legibility minefield, but Wolfenden’s smart, geometric design is eminently readable.
09. Erik Spiekermann
For Spiekermann, type is all you need
Erik Spiekermann is one of the world’s most respected names in type design. The co-founder of FontShop, two of his typefaces, FF Meta and ITC Officina, are considered modern classics. Plus he’s been behind the design of brands such as Audi, Bosch, VW, German Railways and Heidelberg Printing. And his business card conveys a powerful message: once you’ve got the typography of your design right, what more do you need?
-
Digital artists are in for a treat this Bank Holiday weekend as Amazon have got a sale on Wacom and Bamboo gear. That's right, by heading over to Amazon's Shop the Future weekend deals page, artists and illustrators can pick up graphics tablets, pens and gadget cases for less.
You'll also find deals on the latest cutting-edge electronics, home, health and beauty as well as food and drink products.
Let's dive in and see exactly what's up for grabs for digital artists – and how much you can save.
Save 30%: Wacom Intuos Pro Small Graphics Tablet
First up is the Wacom Intuos Pro Small Graphics Tablet. Starting at midnight on 25 August and running through until 23:59 on 30 August, this offer sees the popular tablet retailing for just £161.99. That's a 30 per cent discount off the normal RRP.
Save 20%: Wacom Intuos Photo Pen and Touch Graphics Tablet, Small - Black
Running over the same time is a discount on Wacom's Intuos Photo Pen and Touch Graphics Tablet small black model. Compared to the tablet's regular price, you can save 20 per cent off RRP and snap it up for just £71.99.
Save 42%: Bamboo Stylus Duo 3 for Media Tablet/PC - Silver
This weekend offer sees a huge 42 per cent coming off the RRP of the smudge-free navigation tool. Perfect for smooth handwriting and compatible with most tablets, smartphones and touch screen PCs, this stylus can be yours for just £17.99.
Save 46%: Bamboo Spark Gadget Case - Grey
There's 46 per cent off RRP to be saved this weekend on Wacom's grey Bamboo Spark Gadget Case. Up for grabs for just £64.99, this is an ideal opportunity to snap up this tool, which turns handwritten notes into digital assets.
-
-
-
Drawing with charcoal, pastel and chalk is addictive. Maybe it’s because the results are so fast and immediate, or maybe because the look is so dang cool, but people love to learn how to draw with charcoal. Even the great Michelangelo loved drawing with charcoal.
Whatever the reasons for charcoal's popularity as a medium, and there are many, these charcoal drawing techniques are used by many artists every day. So let's jump in, to reveal some handy tips and tricks.
Check out the video below, then follow the steps to success.
Any type of charcoal will do for these tips. Just ask at your local art store and they will guide you (see point nine for a little about different types).
If this inspires you to educate yourself further, why not head over to Schoolism.com to discover courses, workshops and more. It’s an amazing way to study with the pros.
01. Concentrate on the essence
This image is all about Paul and everything supports or revolves around that main idea or essence
It’s been said, "The main thing is to keep the main thing the main thing." Artistically speaking, the main thing is called the essence. Remember when creating a piece the primary question to be asking yourself is, "What is this image about?", or "What do I want to say?".
Once you settle that – the 'main idea' or the essence – then everything you do from that point on, every move and every detail you put in or leave out, should strengthen the 'main thing' or the essence of the piece.
02. Learn the value of value
Learn how to organise lights and darks
The word 'value' gets thrown around a lot in art and can seem confusing. What we mean by 'value' in art is simply a walk from white to black (light to dark) using one to 10. One is the white of the page and 10 is black, so a five, 50% or 'halftone' is a medium grey, halfway between white and black. Make sense? So every image is composed of values (darks or lights) regardless of colour.
To help you with this, work from the middle out, keeping your darkest dark (the shadows) no darker than a six or a seven value and your lightest (the light effect or everything in the light) a three or four value. Work your way towards the darks (accents) and your whites (highlights).
Think of accents and highlights as twins just living in different neighbourhoods. They are not the most important element of your image. They serve the whole.
03. Use the hierarchy of value
You can control the eye using value. Whaaa?
It’s safe to say that a successful image is one that quickly reads well and has power to touch you. Using value or tone and assigning different areas of the image to lesser or darker tones can be a very helpful tool.
In the image above, based on a photograph by Josiah Bice, the darkest values are used on the subject. Notice the lightest value on his cheek and the darkest value reserved for the mass of his body.
Using a hierarchy of value allows you to direct the viewer to what you want them to see first. In this case, it’s Steve smoking his pipe. Everything else becomes less important. He is the essence of the image.
04. Squint
Squinting your eyes simplifies things
Sometimes 20/20 vision is not helpful. When we observe whatever we are drawing there is a ton of information going in through the eye gate. And an image filled with needless details cripples the effect of a piece. The goal is to edit and simplify.
Squinting our eyes just enough simplifies values and over all helps us to see a simplified version of what we are looking at. Squinting also helps you to see simple shapes very clearly. Nailing those simple shapes helps with the overall essence of the piece.
05. Try thick and thin lines
Not all lines are created equal
Using thick and thin lines is an interesting idea and it’s funny how many artists miss this very helpful concept/tool in drawing. In a drawing, if every line has the same width or is drawn using the same exact pressure it looks like a colouring book drawing and can come across as very monotonous and boring. So using thick and thin lines in your drawing can make it so much livelier.
So how do you use it, and what do you need to know? The simple rule of thumb is that lines on top of things are thinner since light is hitting them and lines underneath objects can be thicker since there are usually shadows underneath things. That’s it. Wow – that was simple. Check out the various dancing lines and thickness on the dog drawing. Now you know.
06. Use an eraser
Sometimes light can be 'erased' out
The cool thing about charcoal is that it’s easy to control it. You can move it around easily. Once you apply charcoal you can remove it or erase out where you don’t desire it. In the picture above, the erased part is marking out where the light is hitting the model's head.
07. Get a few tools
You just might need a tool belt
There are many tools of the trade for an artist, and for charcoals there are cool ones to have. The image above shows some great ones: a really small fine line eraser, a kneaded eraser that you can bend and squash, and a hardcore eraser pen for those tough heavy lifting erasing jobs.
Make a one-stroke mass of charcoal
Using charcoal or pastels requires us to 'move' or apply the medium, and there are many ways to accomplish this. Your finger is the most obvious, yet can be streaky or too small. A Webril Wipe is a great tool for making a large mass in one stroke.
08. Wear a glove
This is an oil-free zone
Did you know that your hand has oils on the surface that can damage the purity of your paper or stock and fight against you? The oils on your hand can even attach to your paper and repel your medium. To stop this problem, wear a glove or place another piece of paper under your hand to protect your artwork.
09. Charcoal pencils
These are a good place to start
Charcoals come in many forms, from pencils to thick sticks to chunks, and whatever you decide to use is up to you. In the above photo are three good examples of charcoal pencils. Know that they can be messy, so afterward using them you can spray your drawing with a workable fixative to control them.
10. Press on
You can fly – just keep on trying
Remember that drawing is difficult and at times frustrating. Stay at it. Creating art is extremely hard to pull off and feeling happy about your progress can take time.
Learning and growing is a community project. Reach out and network with a few artists you admire. Be humble and teachable and ask them for insight about your work. Ask 'What are my weaknesses?' and 'Where should I start or what should I focus on?' Ask them to be honest. Those are good questions and a great place to start.
The good thing is that everyone has been down in the dumps as well, and even to this day there are really discouraging days full of doubt, and yet days where we can fly! So press on and open your wings and jump and catch the wind!
This article originally appeared in Paint and Draw magazine. Subscribe here.
Related articles:
-
Heading to college and not kitted out yet? Maybe you're looking for an upgrade. Either way, this handy list of the best laptops for graphic design students will take you one step closer to being perfectly equipped for your university course. (A subscription to Creative Cloud will take you another.)
When choosing a laptop for your daily design work, there are many things to consider. One is power versus portability: you need something that’s thin and light enough to throw in your backpack, but also powerful enough to run your suite of creative tools.
And you need to decide whether macOS or Windows is right for you. The former used to be the staple of creative professionals, but it really doesn’t matter what platform you use these days.
Whatever your preferences, each of the three machines here will give you all the power and performance you need to hit the ground running with your studies. Read on for our pick of the best laptops for graphic design students.

Microsoft's Surface Book is an incredible machine – even in its lowest spec option. The fact that you can use it as both a tablet and laptop makes it the ultimate digital sketchbook. Just detach the screen and draw using the included Surface Pen, or buy the innovative Surface Dial for £90 and get an intuitive way of controlling your creative tools.
Even better, flip the screen around, reattach it and you can use it to draw at a more natural angle. It’s on offer at £1,299 for the lowest spec at the moment – which is a bargain for such a versatile, powerful creative machine.
Read our review of Microsoft Surface Book.

The MacBook might not have a lot of ports (one USB-C to be precise). And it might not have the power or screen size of the MacBook Pro. But for £1,249 it’s a great option for designing on the go.
A 12-inch screen is at the heart of the MacBook, but you can of course plug it into an external display using an adaptor (via USB-C). And at 2304 x 1440 pixels there’s plenty of real estate.
If you’re feeling a little flush, you can configure it with up to 16GB RAM – plenty for all but the most demanding tasks. Light, powerful and utterly stylish, the MacBook is a fantastic option for design students.

The Surface Laptop is one of the best laptops for graphic design students. Even the lowest-end model at £949 is powerful enough to run Photoshop and Illustrator on a daily basis, and the fact you can use the optional Surface Pen to draw directly on screen makes it even more appealing.
Bear in mind that if you want to run Creative Cloud apps, you’ll need to switch to Windows 10 which is free until early 2018. (The Surface Laptop comes with Windows 10 S – which only enables software from the Windows Store to be installed.) Still, with its sleek looks and fabric keyboard, the Surface Laptop looks great and performs excellently.
-
Every day at the Association of Illustrators (AOI) we talk money – how to make it and, in particular, how to ask for it. Through those conversations with members and colleagues, what is particularly striking is how many creative freelancers subscribe to the self–fulfilling prophecy of being a person who finds dealing with money just all too awkward and difficult.
If we want a career in the industry we love – indeed, if we want an industry at all – we’ve got to get over this issue now. We’ve got to stop talking about our fees (and contracts) as if they are an area of freelance work that doesn’t benefit from a thorough understanding and a degree of willingness to keep ourselves updated.
Licensing know-how
Within illustration, artwork is licensed. Licensing is a win-win situation – the client pays for what territory they need (from single country to global), how it is being used (a brochure or billboard, for instance) and for how long (one year, three years, and so on). Budgets – and fees – will vary hugely.
Licensing means that the illustrator’s fee is proportionate to the overall investment the commissioner is making.
Ren Renwick argues that licensing creative work is a win-win situation
For example, budgets for a print advertising campaign will, by necessity, be far larger than for a social media campaign, and fees will scale as well. While it can be hard outside of the world of global brands to comprehend the scale of budgets involved in commissioning, it can also be easy to assume all commissioners have deeper pockets than they do.
Base fees on usage, not time
What is key, then, is to price your work correctly and then negotiate either on usage rights or on the fee. And that’s why trying to sell creative work based on a time-related rate (hour/day rate) is not appropriate.
It’s not about the time, it’s about the image’s usage
Ren RenwickAn image for a large campaign might take several days but be worth thousands of dollars, for example, so if priced on a time rate the illustrator could receive a fraction of that.
Then again, you might spend a week doing a half-page editorial image, but the fee may be less than what you might charge for a five-day ‘day rate’ job. It’s not about the time, it’s about the image’s usage.
Don't be awkward about getting paid
If you price your work based on sound calculations, and state the fee with confidence, then there is no awkwardness. It is a transaction.
If you simply can’t bring yourself to negotiate your fees and contracts, ask someone to do it for you. Whoever it is – yourself or someone else – they must have the expertise to understand how to price it correctly.
This is one of the many benefits of being represented by an agent, but if you are not represented you can always get support from the AOI. The AOI advises on many significant commissions for very large clients, supporting illustrators to price their work appropriately.
At the end of the day, why are we doing creative work? An element is the pleasure of course, but it’s also to generate income. And it’s fine to luck out by being paid to do what you love! That doesn’t mean you should waive your fee, or reduce it – it just means you should keep abreast of the business side of work as much as the creative side.
This article originally appeared in Computer Arts magazine issue 267. Buy it here.
Related articles:
-
An insecure Apple authorization API is used by numerous popular third-party application installers and can be abused by attackers ro run code as root.
-
Wes Anderson's stylised action-comedy The Grand Budapest Hotel scooped up Oscars for best production design, costume design, makeup and score. As lead graphic designer on the film, Annie Atkins handcrafted Anderson's fictional empire of Zubrowka one postage stamp and pastry box at a time, working closely with production designer Adam Stockhausen and Anderson to bring the cult film-maker's meticulous vision to life.
Atkins has also worked on Laika's stop-motion masterpiece The Boxtrolls, for which she the incredible Victorian packaging worn by the curious underground creatures.
We caught up with Atkins to find out what it's like to work as a graphic designer in the high-profile world of film. Read on for her top tips, tricks and advice.
01. It's not all about the cinema audience
Close up of The Grand Budapest Hotel signage
"When we create graphic props and set pieces, we're not always making them for the cinema audience – these are pieces that are dressed into the sets to create a more authentic experience for the director and actors to work in," says Atkins.
"Every period film you see will have shopfront signage and street posters and offices full of paperwork and maps and documents. These are all items that are made by the show's graphic designers specifically to fit the genre, period, and style of the script. It's about setting up a scene."
For example, the signage for the titular hotel features typesetting inaccuracies taken directly from real references of the period the film was set in.
02. Your props must feel real
The Trans-Alpine Yodel newspaper is full of real articles, written by Wes Anderson
The designer's job is to make props that feel authentic for the actor. Remember: what you see on screen isn't what the actors are facing.
"In real life, film sets don't look like they look in the movies – they're full of lights and cables and people standing around in North Face jackets," smiles Atkins. "So anything you can do to give an actor or director a more authentic experience on set is going to go some small way in helping the final cut of the movie."
Wes Anderson wrote every single article found inside the Trans-Alpine Yodel newspaper that features in The Grand Budapest Hotel. His efforts weren't wasted, either. "There's a lot of waiting around on film sets, so people tend to read the fake newspapers," adds Atkins.
03. Set design is all a trick
A film's art department can be huge, with all kinds of specialists from model-makers to painters, scenic artists, draughtsmen and plasterers.
"Design is rarely neglected in filmmaking, but sometimes it seems invisible because an audience assumes that everything they see on a screen was already there," explains Atkins. "They don't think for a second that it was all built up from nothing on a stage in Bray. That's the magic of design for film: you're not always supposed to be aware of it. It's all a trick."
04. Learn the period quickly
Ralph Finnes asked for his character’s notepad to be personalised with lines, even though the camera can’t see that level of detail
"I usually get around 6-8 weeks prep before shooting starts, and that's the essential time I take to become fully immersed in the period I'm working to," says Atkins. Working on a range of projects means it's usual for her to design for the same style or period more than once.
"I knew nothing about nothing about Eastern European 1930s when I started the Grand Budapest Hotel," she continues. "You need a good understanding of the history of the printing press, for example, to be able to imitate it convincingly on a laser jet."
05. Study antique design in the flesh
Hundreds of hours of research goes into making realistic graphic props for film
The one piece of advice Atkins would offer to design students? Study antique graphic design in the flesh. "There's no point doing a Google image search for a telegram. You need to understand the scale of the text and the texture of the paper in your hands, otherwise it's never going to work in an actor's hands."
06. Be prepared to live on set
It's important to be on set as much as possible
Although sometimes it's possible to work remotely, there's no substitute for getting on set. "Film sets are very physical environments and you need to be there with the rest of the crew wherever possible, so you can go down to the prop house or nip in to the set to take measurements," says Atkins.
"The prop master and the set decorator need you there, so they can grab you and show you stuff as it's being turned out. You also need to see the textures and weights of materials, and understand the scales of sets."
Practical considerations also have an impact – if you're working from home, you need to factor in time to travel to and from the set when required, which isn't always possible if you're working to a tight schedule.
07. Check your spelling
You know you’ve got an original Mendl’s box if there are two 'T's in 'patisserie'
Atkins has one major regret from her work on The Grand Budapest Hotel: she didn't check the spelling on the iconic Mendl's box before it went to print.
"I'd spelt 'Patisserie' wrong – we only noticed it after we'd shot it a hundred times in various different scenes. I was mortified," she cringes. "We corrected it in post, and Wes was so nice about it, but I burnt bright red when I realised what I'd done, especially as spelling and grammar is something I take quite a lot of pride in and go on and on about to junior designers."
08. Last but not least…
Atkins' favourite prop is the book that opens the story
Finally, Atkins has some some quick-fire tips for surviving on a film set. "Never run on a film set – they'll know you've forgotten something. Also: keep your paper supplies high… It's better to be looking at it than looking for it."
Liked this? Try these...
- How to publish your own books on a shoestring
- Why a leading London foundry is letting users trial fonts for free
- The designer's guide to working from home
-
There are a few factors to consider when you're looking for the best laptop for Photoshop work. Firstly, think about where you will be doing most of your work.
If you want a laptop for Photoshop that you can take out and about regularly, you’re always going to have to sacrifice a little portability. If you simply move from studio to studio – as a freelancer maybe – you can get away with a heavier, more performance-orientated machine. If you want a mixture of both, there are options for you as well. But don’t expect them to be cheap.
- Choose your Adobe Creative Cloud plan
We’ve rounded up five of the best laptops for running Photoshop that cover all of these bases – so read on and make your choice.

If you’re looking for all-out power and price isn’t too much of a consideration, check out the rip-roaring HP ZBook Studio G4 – the latest in HP’s line of mobile workstations.
The top-end model isn’t cheap, but it packs incredible specs including a 15.6-inch 4K DreamColor display that can easily be colour calibrated, a blazing-fast Core Intel Xeon CPU, 32GB RAM, a 512GB SSD and NVIDIA Quadro M1200 dedicated graphics with 4GB VRAM. There’s also a healthy range of ports for peripherals and Bang & Olufsen speakers.
At just over 2kg (4.6lbs), it won’t break your back carrying it around, and it’s pretty thin at 18mm.
Read our sister site TechRadar’s HP ZBook 15 G4 review
---

We couldn’t avoid the MacBook Pro with Touch Bar in our list of the best laptops for Photoshop. It’s a phenomenal machine for running powerful programs for all kinds of creative work. The 15-inch model is our top pick, coming with a 2.9GHz i7 CPU, 16GB RAM, a 512GB SSD, and four ThunderBolt 3 ports.
The Touch Bar – while perhaps not quite as cool as having a multi-touch display – is very useful with Photoshop, enabling you to perform quick actions, such as selecting a colour or changing the opacity of a layer, by swiping your finger along the bar.
It's expensive, but build quality is immaculate and the MacBook Pro is extremely portable.
Read TechRadar’s MacBook Pro with Touch review
---

The Razer Blade may be a laptop built for gamers, but it’s an incredible machine for creative professionals as well. As well as seriously looking the part and being light and slim, it packs a huge punch, with a 4K multi-touch display, up to 1TB SSD, 16GB RAM and the latest Core i7 quad-core processor.
You also get Thunderbolt 3 connectivity (through USB-C), USB 3.0 and HDMI output. The GeForce GTX 1060 with 6GB VRAM makes this machine sing for any kind of graphics work.
Oh, and we love the Razer keyboard – which has individually backlit keys, meaning you can create your own lighting effects (we’re sure you could do something creative with your most-used keyboard shortcuts).
Read TechRadar’s Razer Blade review.
---

The Surface Book is at the top of Microsoft's Surface range of products, and you get a load of power, with the convenience of a detachable tablet with multi-touch display that you can use as a digital sketchbook.
The 512GB SSD, Core i7, 16GB RAM, GeForce version is our favourite of the laptop models. And although it's pretty expensive, it’s stonkingly fast and has fantastic build quality.
Bear in mind, though, that you’re only getting a 13.5-inch screen – a fantastic 3000x2000, 267ppi screen – so factor in the cost for a monitor when you’re back at your desk (and indeed the extra Surface Dock for plugging in all of your peripherals).
Read our Microsoft Surface Book review.
---

In its most basic spec, the Dell Precision 7720 is a little underwhelming – it hasn’t even got a full HD display. But, if you’re prepared to spend a little more and get into the customisation options, you can build a dream Photoshop laptop.
For instance, we specced up the 17-inch mobile beast to have a UHD display, a 512GB SSD and a rapid Core i7 for a shade under £3,000 (or $3,130 on Dell's US site).
Sure, it's a lot of money, but remember you’re getting a 17-inch portable workstation here. Of course with that comes the weight: 3.4kg (7.5lbs) to be precise.
Read TechRadar’s Dell Precision hands-on review.
Related links:
-
Designers are spoilt for choice when it comes to typefaces these days, with thousands of paid-for and free fonts to choose from. But what about if you want to make your own? Just like creating a new logo design, developing your own font is no easy feat, and there are many factors to consider when doing so.
One of the most important considerations is kerning; the process of adjusting the spacing between letters to achieve a visually pleasing result. Some designers find it easy, others find it a tricky process where success is achieved more by luck than real judgement. But follow these tips and you should find yourself on the right track...
01. Choose your typeface early on
Settle on your type choices early on and everything will flow naturally from there
Each typeface requires its own kerning, adjustments and attention to detail. So it's important that you make a decisive decision on the typeface you're going to be working with early on within the design process. Making last-minute changes can significantly change the direction of your design as well as the kerning that specific typeface needs. Rushed, last-minute kerning is rarely successful kerning, so don't put yourself in that position.
02. Consider specific letter combinations
Some letters don't kern as well as others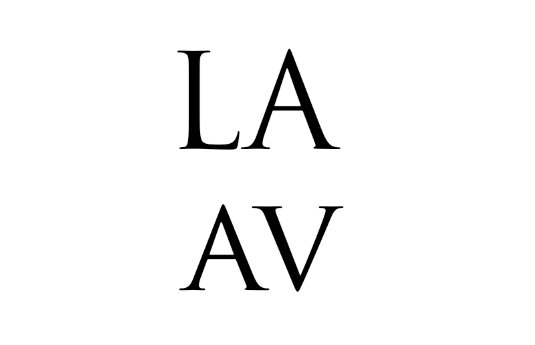
Remember that some letters that don't kern as well as others within a word. Letter combinations such as 'LA', for example, are not as complementary as 'AV'. In such cases, attention to kerning needs to be considered and focused in regards to the negative space.
03. Blur your eyes
Blurring your eyes or squinting can help you focus on letter shapes
While kerning display typefaces (you should only be kerning display typefaces by the way), try blurring your vision a bit by squinting or crossing your eyes. This enables you to focus on the contrast and white space of the letterforms without becoming distracted by the characters themselves.
04. Flip the typeface upside down
Turning the typeface upside down is a good way to examine the letter shapes
Another useful exercise for kerning is to turn the typeface upside-down. This allows you to focus on the form of the characters rather than getting distracted by the actual word being viewed. Upside-down text becomes more abstract and enables you to focus on lights (white space) and dark (the characters) areas.
05. Create rhythm and consistency
The best font kerning has good rhythm and consistency
The best font kerning (and the best typography) has good rhythm and consistency. One character sitting next to another should appear rhythmic and balanced. One way of achieving this is to step back from the monitor and observe the text. Does the text 'box' appear as one equal shade? Or does it appear darker between some characters and lighter between others?
06. Remember spacing between words
Kerning is about controlling spacing, and that includes the gaps between words
The main focus of kerning is usually the spacing between characters, but don't forget the spacing between words. This can be especially relevant when working with free fonts you've downloaded online, which are sometimes poorly constructed in terms of spacing.
07. Supply two versions of a logo
Supply two logos to clients: one for large sizes and one for smaller use
Kerning typefaces for logos can be quite tricky, since logo typefaces can be viewed at very large or very small sizes. I recommend supplying clients, when needed, with two sets: more tightly kerned pairs for large sizes and looser for the smaller uses of the logo.
08. Test yourself
Like mastering any technique, the best and most effective way to improve your kerning skills is through practice. The Kerning Game is a great way to brush up on your technique as well as learning by trial and error the most common mistakes made whilst kerning.
09. Try out a kerning tool
Check out www.letteringjs.com, a jQuery plugin that enables HTML text to be kerned easily
For us really picky, detailed web folk, try looking at Kern.js and Lettering.js. The second one is a jQuery plugin that enables selectable HTML text on the web to be kerned and controlled in other profound ways.
10. Learn your terms
Tracking is about uniform spacing across a text selection
There are lots of specific terms related to typography. For instance, you may hear other designers talk about 'tracking' and assume it's the same thing as kerning. It's not. Tracking is about controlling the uniform spacing between all the letters in a piece of text, while kerning refers to the spacing between two specific letters.
For a full glossary, take a look at our article Typography rules and terms every designer must know.
Like this? Read these!
-
How much time does it take for a brand identity to become stale? For Medium, less then two years seems to be long enough. Earlier this week the online publishing platform unveiled a new logo (above) and wordmark to replace the colourful, three-dimensional logo design it used from late 2015.
Created by Medium's in-house designers and San Francisco-based design and branding studio Manual, the new black and white logo is an abrupt change that calls back to the original look of the site from 2012 through to 2015.
The new logo is sure to be a welcome change for eagle-eyed designers who had a negative reaction to the Medium 2.0 rebrand. While the vibrant 2015 design (below) came under scrutiny for its inconsistent corners and the questionable quality of its 3D effect, the 2017 logo takes a more mature approach with flat, sleek letter shapes.
The three dimensional 2015 Medium logo received a mixed response from designers
When looking through the evolution of the Medium brand, the new logo looks like a logical refinement of the site's original monogram (below). The glyphic serifs give Medium an authoritative editorial look that also manages to appear more personable than the square corners found on the platform's first identity.
The site's original logo, from 2012, was authoritative, with square corners
This brand journey, circling back to a mature and sophisticated look, only helps to highlight Medium's 2015 whacky phase. While the colourful logo was certainly fresh and distinctive, perhaps it deviated too far from what Medium wants to be known for.
The 2017 identity does include a nice range of tasteful palette options, though, which Medium might not have hit upon if it didn't experiment with colour before.
The new Medium logo includes a wordmark and colour palette
The good news for Medium is that plenty of designers appear to like this refined rebrand. Many have already taken to social media to sing the praises of the new look and crack a joke at what has been appropriately described as the 'teenage phase' of the 2015 logo being over.
However, many were left scratching their heads as to why the 2015 design was scrapped so quickly. Whatever the reason, let's hope it's a case of third time lucky for the site.
Related articles:
-
-
In this guide I’ll talk about the processes I use when creating artwork in InDesign for special finishes such as varnishes, foil blocking, embossing and die cutting. Each finish has some best practice guides you should follow, but once you get your head around creating one you should be able to easily apply this knowledge to the other processes.
To illustrate each print finish, I'll use an example of a cover I created for Computer Arts in collaboration with Celloglas, a specialist in decorative print finishes. At the bottom of each page you'll find a video showing each design being brought to life at the printers.
On this page I'll teach you how to create foil block designs in Photoshop. Use the drop-down above to find out how to tackle spot varnish (page 2), die cuts and folds (page 3), and embossing and debossing (page 4).
Foil blocking
Issue 232 features a diffuser foil, fluted emboss and a spot UV
It's always best to create the artwork for foil block printing as a vector. If that's not possible then you want the artwork to be a minimum of 600 DPI – this will help you avoid jagged edges and keep the foil blocking look crisp. Remember, you can’t achieve gradients or shading with a foil, so the artwork needs to be a solid colour.
Generally, you'll get the best results when you're not trying to line the foil blocking up with a printed image, as paper stretch/shrinkage can cause the foil to misregister.
Best practices
- Avoid using any foil lines thinner than 0.5mm/1pt
- Leave at least 1mm space between the separate foiled elements to stop shapes bleeding into one another
- Don't try and align the foil to fine details such as small type (especially serifs) or thin lines
- When lining up the foil with a printed image, add a 1mm to the foil guide to allow for misregistration
- Large areas of solid foil can be tricky to get right and you may not always get the best results
Creating foil blocking in InDesign
The printed cover and the diffuser foil guide
I find the easiest way is to supply your foil blocking artwork is as a separate PDF file. I tend to design the document as a mockup, using a block colour to represent any foil elements, then add the foil block elements to my final print artwork.
This means you can see the closest example of how the final printed product will look, and reduces the risk of any misregistration issues. It also means you have a mockup version ready to send to the printers.
- Finalise your design, with the foil block elements in a solid colour on a separate layer over the top of your print artwork
- Duplicate the page three times. One page will be your mockup, one will be the final artwork for printing, and one will be the foil block
- Delete the unwanted elements from the relevant pages, and save each version with the relevant name
- Open the files and delete the unwanted pages from each file
- In your foil document, change the colour to solid black, and check to make sure you've covered everything by turning off the black ink and looking in your Separations Preview panel
- Some printers may require you to set up a spot colour and work with one document. In this case, make sure the spot colour is set to Overprint (via 'Window > Attributes') so you don’t lose any of the detail underneath the foil block element
It’s always best to talk to your printers or finisher to check how they would like the file to be provided and for any special requirements. If you have any concerns, ask if you can send over an early example and get the professional's input.
Next page: Spot varnish
Spot varnish
The great thing about spot varnish is that you can align it with various elements to really accentuate particular parts of the design. It also works really well when you're using it to add interest or a decorative element to a piece.
There are several different options out there for spot varnishes: gloss, matt, soft touch, rough touch, even glitter and scratch-off latex (as we used on our cover below). And you can create some really interesting effects when you mix two contrasting finishes together.
Issue 259 features a scratch-off silver latex varnish
How to
You don’t have the same limitations with spot varnish as you would with foil blocking, as a slight misregistration isn’t going to be so obvious. Like foil blocking, I find the best way to supply the artwork is as a separate PDF file. I use the method I did with the foil blocking, working over my final printing artwork.
If you're using a Photoshop file that's been placed in InDesign, make sure you're working with a solid black by setting the colour mode to greyscale in Photoshop. Again you can check the colour via the Separations Preview panel.
The printed cover and scratch-off varnish guide
Best practices
- Don't use spot varnish over areas that are to be folded, creased or trimmed or glued
- Very large solid areas of varnish may have a ‘pinholed’ appearance, which is not always possible to eliminate
- Mesh selection will vary depending on the image selected – the lower the number, the greater the volume of varnish/coating applied
- For the vast majority of ‘normal’ gloss UV screen work, a 150 mesh will be used
- Varnishes such as glitter require a coarse 21 mesh, and applications such as latex, need a 70 mesh
Next page: Die cuts and folds
Die cuts and folding
Issue 250 featured a die cut, and a spot UV with soft-touch laminate
As with foil blocking, for the best result you want to create your die lines as a vector graphic. I use solid lines for areas that need cutting, and dotted lines for the areas that need to be folded. Once again, you want to work over the top of your print document.
When designing your artwork, remember you'll get the best results if you don't try to align the die to a printed image, as there is always the chance of a slight misregistration.
Best practices
The printed cover and die cut guide
There are some general rules of thumb to take into consideration when creating your artwork.
- Mark up die cuts with solid lines and folds with a dotted line
- Die cut holes need to be at least 4mm, and the lines at least 1pt thick
- Leave at least 2mm space between the die cut holes
- Remember, the more holes or the larger the holes, the weaker the paper/card will become
- Consider the shape of your die cut – be wary of anything that could easily catch and rip
If you're attempting to create anything complicated, it is always best to contact your printer/die cutter first. Every design has the potential for unforeseen problems.
Next page: Emboss and deboss
Emboss and deboss
Issue 262 features a spot UV, a matt laminate and an emboss
Although the terms are sometimes confused for one another, embossing and debossing are two different techniques. Embossing is when a design is pushed up into the paper so it creates a textured relief above the surface. Debossing is when an image is pushed down into the paper so it lies below the surface, creating an indentation.
You can create some great results by aligning an emboss or deboss with your artwork to enhance certain areas. Alternatively, a blind image embossed or debossed onto a solid colour can look very effective.
Best practices
The printed cover and the emboss guide
- Avoid embossing or debossing very fine lines, as this doesn't tend to work
- Try to leave around 2mm space between embossed/debossed lines
- You can create a double-layered emboss and have elements at different heights – just be aware that the more layers you add the weaker the paper becomes
Combining different finishes
Combining these different techniques can take a bit of thought and preparation. It’s good to know you can’t foil over a varnish, so if you want to use these finishes together remember to leave the foil area out of the varnish. Embossing and foil works well together, so long as you don’t over-complicate the design. Finally, if you're including multiple special finishes on one document, make sure you clearly name the PDFs to save any confusion.
Related articles:
-
Adobe applications Photoshop, Illustrator and InDesign are the gold standard for graphic designers. These are the tools you'll need to know how to work with if you want to get ahead in the field of graphic design, and you can master these programs with the Graphic Design Certification School. Get a lifetime subscription to the service on sale now for 96% off the full retail price!
If you want to work as a graphic designer, you're going to need to have at least some familiarity with Adobe's Creative Cloud programs. The Graphic Design Certification School will teach you how to master Adobe's most powerful tools – Photoshop, InDesign, and Illustrator.
You'll get tons of actionable lessons taught by experts who will teach how to bring your ideas to life. You can also get certifications to prove your skills after each course.
Each of these three Graphic Design Certification School courses is valued at $399, giving a full value of over $1,197 for them all. But this offer means you can get this incredible bundle of courses on sale for 96% off the retail price! That means you pay just $39 (approx £30) for a bundle that will help you prove your skills, so grab this deal today!
This great deal comes courtesy of the Creative Bloq Deals store – a creative marketplace that's dedicated to ensuring you save money on the items that improve your design life.
We all like a special offer or two, particularly with creative tools and design assets often being eye-wateringly expensive. That's why the Creative Bloq Deals store is committed to bringing you useful deals, freebies and giveaways on design assets (logos, templates, icons, fonts, vectors and more), tutorials, e-learning, inspirational items, hardware and more. There are even top competitions like the popular iPad Pro Giveaway.
Every day of the working week we feature a new offer, freebie or contest – if you miss one, you can easily find past deals posts on the Deals Staff author page. Plus, you can get in touch with any feedback at: deals@creativebloq.com
-
In recent times, the worldwide market has seen a dramatic increase in mobile app usage, and with it a big increase in revenue figures. However, about one in four users tend to abandon mobile apps after just one use. To halt such an alarming trend, mobile app developers need to work to provide a great user experience and make the introduction process smoother.
This is where user onboarding comes into picture. Providers of mobile app development services (such as Oxagile, where I work) typically recommend one of the following common types of onboarding:
- Benefits-oriented
- Function-oriented
- Progressive
In this article, we'll look into each technique to see how to effectively employ it. Use the drop-down above to navigate to each different type of mobile onboarding.
Benefits-oriented onboarding
You can use this method of onboarding to introduce the main benefits of a product, show users what perks they can expect and explain how those perks can be used in daily life. When applying benefits-oriented onboarding, there are some steps to follow. I'll run though them now.
01. Show one perk per screen
Keep benefits to one per screenNo matter what number of benefits you decide to unveil, it’s paramount you stick to the 'one benefit per screen' rule. This way you won’t clutter your screen with too much information and will draw users’ attention to key points.
02. Don’t limit yourself to just three benefits
Without doubt, three is a magic number, but sometimes it may be useful to introduce more than three benefits. Just don't go overboard – when trying to show the app in its glory, you don’t want to bore users with too much information.
03. Be concise
Verbs can help secure users' attentionUse appropriate vocabulary while introducing your app. Remember that one of the best ways to capture attention is to use verbs – here 'book', 'manage', 'check' and 'rate' give a strong call to action related to the app's key uses. Moreover, avoid lengthy descriptions – save them for app stores.
04. Save signup for later
Let people who are in a hurry to sign up do soOnboarding represents an overview of your app. Going through this overview, the user should understand whether it's worth signing up. That’s why it is logical to put onboarding first and save users from being interrupted by benefits when they have already started exploring the app. However, to please those who want to skip some screens and get started right now, it's worth placing the signup option on each screen.
Next page: Function-oriented onboarding tips for mobile apps
The function-orientated onboarding technique is pretty self-explanatory. Try your hand at it when your goal is to make it clear how to handle your app, show core functionality, and explain when users should rely on one or another function.
Here are some things to consider when employing function-oriented onboarding:
01. Explain one function per screen
Focus on one element per screenAs with benefits-oriented onboarding, strive to simplify the process and avoid an overload of information by explaining one function per screen, clearly and concisely.
02. Try in-app hinting
Handy tips can help explain ambiguous elementsExplain your app’s functions by using hints or button labels. However, avoid describing things that are crystal clear. Like the entire app, your onboarding should provide true value to users. It’s pointless to describe such obvious elements as toggles, back and forward arrows, or close and cancel buttons [x].
03. Help users get started
Make sure your empty states aren't off-putting
If your app welcomes users with an empty screen, it will likely cause confusion – they won’t understand how to start using it and may think there is a bug. That’s why it’s essential to include a note, such as 'tap to add items' to help them start.
04. Let users skip to registration
As mentioned in the previous technique, allow users to skip introduction screens and to register easily at any stage of onboarding.
Next page: Progressive onboarding for mobile apps
One of the best ways to learn something is to see it in practice. Progressive onboarding relies on this idea. With such an approach, you introduce the app's features when users have actually started looking into it.
Below you can find advice on implementing the progressive onboarding technique.
01. Introduce hidden functions
The Feedly app offers a wealth of ways to share an article (via Twitter, G+, email, and so on). To avoid cluttering the navigation bar, it employs hidden functionalityEvery mobile app developer aims to use the mobile screen space as effectively as possible, which means tricks such as expanding menus and hidden functionality are relatively common. In this situation, it’s a good idea to explain where those hidden functions are through onboarding.
02. Explain gesture-driven apps
Let users know how gestures work on your appIf your app is quite simple and relies heavily on gestures, the progressive onboarding technique is ideal. When onboarding, explain the function of each gesture through pop-up messages to users.
03. Offer further explanation
Provide a gesture cheatsheetIf your app uses a lot of gestures, it will be difficult for users to remember them all. Moreover, it's likely your app is not the only gesture-driven one in a user’s phone. Make things even more straightforward by explaining gestures in the app’s settings, so users can refer to them whenever they need to.
Combine onboarding options
The Human app onboarding combines benefits- (screens #1 and 2) and function-oriented (screen #3) techniquesThe types of onboarding we've discussed here are the most popular ones. However, to successfully compete in the mobile app development space, you can adopt a complex approach by combining two or even three techniques.
When experimenting, make sure such a combination adds high value and doesn’t pad your app's onboarding out.
Read more:
-
Squashing bugs in your animation is a chore, but it has to be done
Flash may have fallen by the wayside, but animation on the web is bigger than ever, and it's at the forefront of providing a compelling user experience. But whether you're using JavaScript, SVG or CSS3 animation, at some point you'll have to roll up your sleeves and get debugging.
Here, some leading developers reveal the tools they use to iron out all the bugs.
1. Chrome's Inspect Element tools
Chrome's DevTools include tools to inspect elements
"Generally speaking I like to use the Chrome DevTools Inspect Element tools, which are getting better every day," says Easee founder Steven Fabre. "Instead of typing everything manually or doing the back-and-forth from cubic-bezier.com to your text editor, you can now change the animation's speed and easing with a slider and visual cubic-bezier graph editor.
"Once I'm happy with the timing and easing of the animation, I like to enable paint flashing to identify and fix elements that may potentially make the animation jerky."
02. CodePen
CodePen will flag any syntax errors
Designer and developer Dudley Storey reduces the need for debugging from the start. "I avoid typos by writing CSS animations in Sass," he tells us, "using either CodePen or CodeKit – both of which flag syntax errors.
"If I am stuck with an unexpected result, I work backwards: one simple check is to set my CSS animation(s) to a single to { } declaration, which allows me to ensure the elements I'm animating can actually reach their final states."
03. Firefox Developer Edition
Firefox's Developer Edition is packed with debugging tools
"CSS animations and transitions can be tricky to debug," says web animations advocate and consultant, Rachel Nabors, "especially in UI animation, where the movement is often very quick. That's why I like Firefox Developer Edition's animation tools so much.
"In the animation panel, I can scrub through an animation or even a group of animations to see what's actually happening. If an animation has already run, I don't need to refresh the page, just back that playhead up."
04. GreenSock
GreenSock offers a suite of tools for JavaScript HTML5 animation
Senior UX engineer Sarah Drasner has a top tip for debugging JavaScript animations. "I usually use GreenSock," she tells us, "which comes equipped with timeScale(value). This handy function enables me to slow a whole timeline down so I can see how things are interacting.
"There's also timeline.seek(value), which enables me to find a specific place in time. The longer the animation, the more helpful this tool will be to your workflow."
05. Trial-and-error
At Generate London, award-winning web animator Chris Gannon will share his processes and explore some of the tools he uses to build them"Animations play an important role in user interactions," notes Patrick Brosset, DevTools engineering manager at Mozilla. "Specially crafted animations not only look good but can help users make sense of changes in a user interface. Getting the perfect animation, fine-tuned to progress and last just the right way, is a trial and error process.
"Tooling is key. Debugging animations requires you to be able to see and edit CSS key frame rules right in the browser, and live edit complex cubic-bezier curves. But more importantly, being able to pause, seek, slow down or speed up an animation and edit its properties at any time is essential. Both Firefox and Chrome's developer tools enable you to do just this."
06. Canary animation inspector
Web motion designer Val Head is another fan of Chrome and Firefox's developer animation tools. "These animation inspectors have saved me loads of time," she reveals. "I use these because they have the most features (though some are experimental). Both have visual timelines and cubic-bezier editors for individual animations.
"Canary's animation inspector is my current favourite. The editable timeline, playhead scrubber, and playback speed control let me get a really good look at what's happening in the code."
07. Your own library
Bryan James's website shows he has a large library
Freelance interactive designer and creative coder Bryan James takes a more organic approach to ironing out animation errors. "I don't debug animations in any particular way," he says, "it's purely trial and error. Recently, I've started using my own small personal group of transition sets that I tend to stick to, so I'm getting quicker at spotting errors with just my eyes.
"My transition set is a group of variables declared as descriptive names, for when particular eases are necessary – akin to the standard set of ease-out, linear and so on, but a lot more bespoke and varied."
This article originally appeared in net magazine issue 279.
Want to learn how to push the animation boundaries? Award-winning web animator Chris Gannon will dissect some of this work at Generate London on 21 September, while Leonard Souza will demonstrate Webflow's new Interactions 2.0 feature the next day. The event will also cover web performance, UX strategy, accessibility, responsive components, adaptive as well as conversational interfaces, user research, prototyping and much, much more. Reserve your spot now!
Related articles:
-
To be a good designer, you need to keep learning new techniques and skills – and what better way to stay ahead of the curve than with a free course for designers. After all, the more diverse your skillset, the more appealing you'll look to employers. The more you learn, the more impressive your work will be.
However, finding good learning resources is a task in itself. That's where Udemy comes in. This online learning platform is aimed at professionals, and there's a ton of stuff on there to help out knowledge-hungry designers.
We've rounded up 10 of the best free courses on Udemy for designers, to give you a taste of what to find on the site.
In this list we've tried to cover all bases, looking at courses that will help you pick up new skills from 3D art to digital character design to Adobe Creative Cloud programs to working with WordPress and beyond. Head over to Udemy for yourself to see the full gamut of courses on offer.
01. Introduction to KeyShot for Digital 3D Rendering
KeyShot is one of the easiest and fastest 3D rendering programs around
In this one hour on-demand video you'll learn the basics of KeyShot and how to use the powerful 3D rendering software to create stunning content of your own. You'll also pick up how to navigate and import your own game assets. All you need to get going is KeyShot 3D rendering software and your own working 3D asset.
02. Adobe Illustrator Essentials for Character Design
Turn your sketches into pitch-worthy art with this course
Turning paper drawings into products that you can sell is the dream of plenty of aspiring artists. With this Adobe Illustrator course you'll learn how to do just that. Thanks to two hours of on-demand video, you'll also master the Overshoot Technique and how to draw on a tablet or with a mouse.
For more Illustrator learning, check out our 100 amazing Adobe Illustrator tutorials post.
03. Adobe Flash CS5.5 for Beginners
Start creating interactive content with these CS5 tutorials
You get a lot of bang for your non-bucks in this free course packed with over 10 hours of on-demand video footage. By the time you're done watching, you'll know how to create animated scenes with Flash CS5.5. Plus you'll learn how to import graphics from Photoshop and how to create web-ready videos with usable playback controls.
04. How To Make a Beautiful WordPress Website Without Coding
Create an online presence in under 70 minutes with this course
Creating a website is one of the most important ways to get your work out into the world. This beginner-friendly course teaches you how to quickly and easily set up a self hosted website thanks to two hours of on-demand video. You'll also learn the basics and fundamentals of WordPress, as well as picking up how to edit and update your site.
For more WordPress learning, check out our 25 brilliant WordPress tutorials post.
05. How to Animate Logos for Companies and Brands
Learn a real skill with business value in this After Effects course
Motion graphics can often appear more complicated than they actually are. This course aims to remove the frustration from learning After Effects and quickly give animators a practical skill they can pitch to clients. Taught over four hours of on-demand video, this course requires you to have access to After Effects.
06. Start Making Comics with Manga Studio 5 / Clip Studio Paint
Learn graphic novel essentials with this course
Always wanted to create a comic book but never been sure where to start? You're in luck, because this course teaches you how to sketch and ink directly in Manga Studio 5/ Clip Studio Paint, import art, paint digitally, set up comic book pages and storylines, and much more. After you're done with the six hours of on-demand video you'll be well on your way to having your own comic.
07. Make a Wordpress Portfolio Website
Start displaying your content to the world!
We've already seen how to make your own site on this list, but what if you're looking for a specific way to show off your dazzling work to potential clients? Enter this course, which runs through how to make a WordPress portfolio site in just two and a half hours of on-demand video. Who knows, maybe it'll help you land your next gig?
08. Backgrounds and Assets for Animation with No Drawing Skills
This beginner's course will give a sense of place to your animations
If you've got rudimentary PC skills, this course will be able to help you produce images and backgrounds for animations. You don't even need immense drawing skills, as this course will teach you how to texture and trace over existing images.
09. Learn 3D Modeling: Blender Basics in Under Two Hours
Quickly add 3D modelling to your skill list with this course
Don't have any prior knowledge of Blender? Doesn't matter. This one-hour course will show you the basics of the 3D modelling software, equipping you with the knowledge to start using tools, shortcuts and primitive objects. All you have to do is install Blender and you're ready to rock and roll with this course.
Once you're ready for more Blender learning, check out our Brilliant Blender tutorials post.
10. Photoshop for Web Design Beginners
Make a clean and simple web page design with this course
Sometimes the best way to learn about a tool is to dive in and start working on a project. That's just what this course, made up of two hours' of on-demand video, aims to accomplish. By creating a web page design, you'll pick up the basics of Photoshop in the process and come out on the other side with a firm grasp of the software.
Related articles:
-
If there's something that never goes out of fashion in the world of design, it's tattoo art. Designers simply love getting inked up with awesome tattoos, and tattoo artists are forever pushing the boundaries of what can be done; check out these mind-blowing 3D tattoos, for example.
Right now, though, we're obsessed with watercolor tattoo art, in which artists recreate the unique look of watercolor paintings in tattoo form. It might look easy but it takes an enormous amount of skill to convincingly ink a replica of the distinctive colour washes and paint splatters that you'll find in a watercolor painting; here are 16 amazing examples by some of the world's leading practitioners.
01. June Jung
Watercolour washes and geometric outlines
June Jung was one of the early adopters of the watercolour tattoo art trend, and has gone on to gain a worldwide reputation for her work. She starts out with realistic-looking designs and adds watercolour effects around them. June appeared in an episode of The Art of Ink, talking about her inspirations and approach. Watch it below.
02. Joanne Baker
Baker also shares her initial sketches on her Instagram
Joanne Baker is a tattoo artist at Semper in Edinburgh, UK. She specialises in animal-based watercolour tattoo designs, and her Instagram account includes majestic crows, delicate seahorses and an angry-looking seagull (someone has to love them, we guess). She also shares her initial sketches, which are works of art in themselves. This rainbow-hued jellyfish design took two days to complete.
03. G.NO
G.NO's beautiful floral watercolour work
This sprawling floral work is a good example of G.NO's signature style. She also specialises in delicate, miniature tattoos and work that looks botanically accurate. G.NO is at Tattoo People in Toronto.
04. Russell Van Schaick
Russell tackles unconventional subjects
Describing himself as an "abstract watercolor tattoo artist", Florida-based Van Schaick's tattooing journey began in Minnesota before he took the leap down to the sun-filled land of Florida. He is currently based out of Hart & Huntington in Orlando and says he's still learning. But, with stunningly vibrant works of body art with lines that flow and colours that bleed into one another so effortlessly, it's clear he's nailing it so far.
05. Candelaria Carballo
Candelaria Carballo's work shows her eye for fashion and style
Carballo has her fingers in many pies; from make-up artistry and tattooing to painting and illustrating. There really is nothing creative she can't master. The Argentinian artist, has a penchant for whimsical, pastel coloured watercolour skin art, and we adore the "rough around the edges" sketchy line-work, very reminiscent of mid-century fashion illustrations.
06. Rodrigo Tas
Tas is a trained graphic designer
Tattooist and graphic artist Tas draws on any surface he's presented with. He's tried his hand at everything, including teaching and is a qualified graphic designer – but since he discovered the pull of the tattoo machine he's never looked back.
Tas' designs blend his eye for graphic qualities and design with his experience with illustration, motion design and art history. The São Paulo-based artist takes up surprise guest slots all over the country.
07. Alejandra Idarraga
Alejandra also creates murals and sculptures
Alejandra Idarraga is a Colombian tattoo artist based in Miami, working at Tattoo&Co. As well as being a tattoo artist, she also creates murals and sculptures. Idarraga's tattoo work ranges from intricate, geometric designs to vibrant watercolour tattoo art, complete with paint splashes and drips.
08. Lianne Moule
UK-based artist Lianne creates picture-perfect watercolours on skin
Lianne is a versatile artist who works across a variety of media, but her speciality is watercolour tattoos imbued with breathtakingly realistic sunlight effects.
Driven by a love of nature and bright colours, she creates her work by first making a watercolour study to use as a reference that she then painstakingly recreates in tattoo form, making sure to include hard-to-imitate spills, splashes and drips by way of a signature. You can find her at Immortal Ink in Chelmsford, UK.
09. Victor Octaviano
Victor creates his stunning works straight onto clients' skin
Hailing from Brazil, tattoo artist and self-taught illustrator Victor Octaviano has been exploring the possibilities of creating a watercolour look in tattoo form for a while now. He loves the challenge of conveying the look and texture of watercolour paintings in his tattoo work, mixing up sharp, energetic brush strokes with gloriously liquid washes, splatters and stains.
10. Ivana Tattoo Art
You'd be forgiven for thinking someone took a paintbrush to this person's arm
Currently living and working in Los Angeles, Ivana is a multi award-winning tattoo artist who's in demand at tattoo conventions worldwide. She describes her work as innovative, sophisticated, and eclectic; a mixture of multiple genres combining funky, bright colours and abstract elements with street style and high art. We love the expressive splashes of colour in this playful image of a Japanese doll.
11. Dêner Silva
If you've wondered about the sort of work that goes into creating a watercolor tattoo, this video from Brazilian tattoo artist Dêner Silva should cast a little light on the process. It shows him creating a distinctive Cheshire Cat tattoo, starting from a reference work that he turns into a line art transfer, and then painstakingly inking the design. Impressive job!
13. Ondrash
Ondrash's sought-after tattoos are as individual as his clients
It's not easy to get an appointment with Ondrash. A versatile artist and tattoo artist with a background in fashion design and conceptual art, he likes to give every client his full attention and so only takes one booking a day at his studio in Znojmo in the Czech Republic, taking time to understand what his client is after, create a reference painting. Only then does he go to work with the needle to create a tattoo as individual as every customer.
-
Zerodium announced new $500,000 payouts for zero days in secure messaging apps such as Signal, WhatsApp and others.
-
An exploit dubbed ROPEMAKER relies on taking advantage of email design functionality, namely by remotely changing CSS in HTML-based emails after they've been sent.
-
CSS3 properties opened a multitude of new doors to web designers and developers, making it possible to create animations and interactivity entirely in CSS markup, without going near Flash, Silverlight or After Effects. Below we've rounded up some of the best CSS3 animation examples around – including standalone effects and sites.
01. One Shared House
Anton & Irene's web documentary uses CSS Transformations
One Shared House is a web documentary profiling UX designer Irene Pereyra's experiences growing up in a feminist commune in 1970s Amsterdam. From the moment you arrive, you're not alone: your cursor movements are followed.
Instead of relying on trite scrolling techniques, Pereyra and partner-in-design Anton Repponen drew inspiration from the early-90s game 'Where in the World is Carmen Sandiego?' and made use of the bottom screen to subtly expose exploratory content, offering you the ability to define your own level of involvement with the story.
Interactions combine with storytelling to deliver a mesmerising, novel experience. Pereyra and Repponen's boldness in persevering through two years of self-funded and self-initiated work is important: "It enables us to experiment with disciplines and techniques for which there is typically no space in client projects," says Pereyra.
02. Type Terms
An animated cheatsheet for type
Type Terms is an animated cheatsheet created by Supremo, a web design agency in Manchester. After doing some research, they found that most existing online information about typographic terminology used simple, static images. The team was looking for a reason to experiment with SVG and CSS animation, and this was the perfect opportunity.
"I decided to create something that was more visually engaging, which would help new designers learn all the key typographic terms in an instant," says designer Dan Heywood.
The team emphasise the importance of designers having a good grasp on typography. For those learning the rules for the first time, or for experienced designers needing a refresher, this cheatsheet is both educational and a delight to explore. The content is focused, the information is clear, and the animations are silky-smooth.
03. Waaark
Mouse over the boundaries for a fun animation
Every interaction on Waaark’s site reveals an incredible attention to detail. Art director Jimmy Raheriarisoa and frontend developer Antoine Wodniack, the individuals who make up the French studio, have thought through everything. They have planned how scenes transition from one page to another, how text fades in a certain way, and how complex SVG graphics animate in.
Everything is brought to life while maintaining performance and accessibility. The pair have added keyboard shortcuts and swiping gestures to make the experience better for people with a wide range of motor abilities.
When asked about their newly released portfolio site, Wodniack explained that collaboration was key: "With the web becoming more and more creative, it’s becoming vital to assemble a creative duo between a developer and a designer. Developers always need new challenges to blossom, and designers need solutions to make their ideas possible."
04. Periodic table
At the start of the demo, the disparate elements gently fly towards each other
The periodic table of elements is a popular subject for designers to showcase new web technologies. Built by Barcelona-based web designer Ricardo Cabello – best known within the community as 'Mr Doob' – this demo starts with the animated elements hurtling through space towards each other to form a table.
You're then given the option to rotate them in three dimensions by dragging on your mouse. You can also switch between 'Table', 'Sphere', 'Helix', and 'Grid' views by clicking the buttons at the bottom of the page.
Cabello created the experiment to see if he could use his three.js JavaScript library to replicate the effects used in a demo for the game engine famo.us. Cabello has also posted this video of how the demo runs on an iPad 2:
05. CSS Creatures
What will your CSS creature look like?
We all know that working in the design industry can sometimes become monotonous. So, take some time out from your busy schedule and have some creative fun with this cute little CSS project from Pittsburgh-based web designer and developer Bennett Feely.
CSS Creatures allows the user to design, create and animate their very own web-based friend. Like the sound of that? All you have to do is send a tweet to @CSSCreatures with your preferred colour, personality and features. Your CSS creature then appears on the site in under 25 seconds!
06. AT-AT Walker from Star Wars
AT-AT Walker by Anthony Calzadilla
This illustrated animation of AT-AT Walker from The Empire Strikes Back by Anthony Calzadilla is created entirely in CSS3. Click on the ‘view the bones’ link on the iPad and you can see how each part animates and functions.
07. GT America
Designer Josh Schaub's animations bring this microsite to life
Grilli Type, a Swiss type foundry, has struck gold with the release of its new font GT-America, and this "fun, funny, fresh microsite that takes the idea of a type specimen to the next level" (in the words of graphic designer and critic Michael Bierut). Every detail on the site fits together to tell the story of the font.
GT-America is named after its country of inspiration, the United States. There's so much play going on here, with more than 40 quirky animations by designer Josh Schaub. You can even interact with some of them to bring the illustrations to life. We like the use of animation and video to showcase the incredible versatility in the font: width, stroke, kerning, use. Everything is a storytelling moment, a teaching moment and a learning moment in one.
08. Caaaaaaaat
The cat stretches to the width of the browser window
Japanese web designer and interactive director Masayuki Kido, aka Roxik, has created this animated kitty which stretches across the length of the browser window, and resizes accordingly as you reduce the window's width. Make it narrow enough and the word changes with hilarious consequences. And the fun doesn't end there - but we don't want to spoilt it, so go have a play now!
09. Greenwich Library
This site uses animation effects to create the illusion of drawing elements while the user scrolls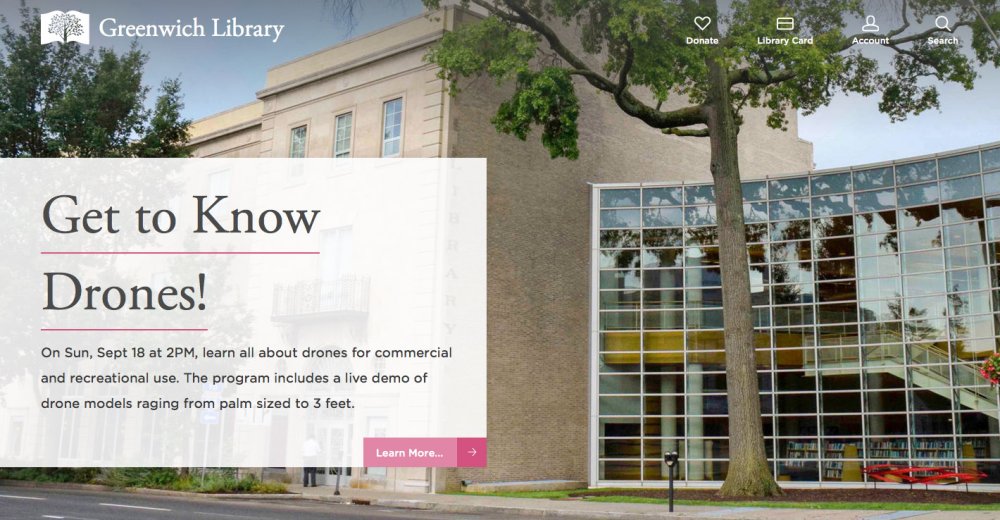
Public service websites don’t have a great record of being beautiful or easy to use, but Greenwich Library’s website is an exception to the rule. The redesign is the result of two years’ worth of research, user testing and design.
One of our favourite parts is the illusion of drawing elements while the user scrolls. This is a trick many developers create explicitly with SVG, but the simple combination of CSS transformations and layering elements here creates just as interesting an effect as a more complex SVG line drawing. The colour-coded navigational elements also add personality without having to splash colour over every element.
10. Interactive album covers
Album covers by bluedashed.comNot only have @MrDenav and @lucasmarinm of bluedashed.com recreated some classic record covers using pure CSS, they've also made them react to music. Demonstrations include First Impressions by the Strokes and Joy Division's Unknown Pleasures. NOTE: Only works in Google Chrome.
Read more:















20 perfect font pairings
in Ειδήσεις από τον χώρο του Design και Hosting
Posted · Report reply
Finding font pairings that set each other off, don't fight the eye for attention, and harmonise without becoming homogenous and dull is tough for graphic designers. The age-old rule goes as follows: concord or contrast, but don't conflict.
But with so many professional typefaces and free fonts to choose from, how do you find two that work in harmony? Here we bring you top font pairing tips, followed by 20 examples of perfect font pairings.
Tip 1: Use font superfamilies
The easiest way to find perfect font pairings is by using different fonts within the same overarching typeface family. Find a so-called 'superfamily' and you'll have a ready-made range of weights, styles and classifications that are specifically designed to work together.
A good superfamily will include serif and a sans serif version of the same typeface: famous examples include Lucida/Lucida Sans and Meta/Meta Sans.
Tip 2: Pair contrasting typefaces
Contrast, as the name implies, is about finding totally different, but still complementary typefaces that are each fit for their intended application. Traditionally, this involves pairing a serif with a sans serif.
Typefaces will generally conflict if they are too similar: two ever-so-slightly different serifs or sans serifs rarely creates nice font pairings.
As a designer, the important thing is to establish a clear hierarchy. This could be as simple as varying size and weight of the same typeface, but where the typeface varies, that's where careful font pairing is crucial. If you have a display face packed with unique personality, you'll need something more neutral to do the hard work.
Tip 3: Pair type sub-categories
Of course, 'serif' and 'sans serif' are themselves broad classifications – each split into several sub-categories. Generally speaking, Old Style serifs such as Bembo, Caslon and Garamond will combine well with Humanist sans serifs, such as Gill Sans and Lucida Grande.
Meanwhile, Transitional serifs have a stronger contrast between thick and thin strokes – examples include Bookman, Mrs. Eaves, Perpetua and Times. These pair with Geometric sans serifs such as Avant Garde, Avenir, Century Gothic, Eurostile, Futura and Univers.
Finally, Modern serifs have an often very dramatic contrast between thick and thin for a more pronounced, stylised effect, as well as a larger x-height. Included in this third sub-category are Bodoni, Didot, New Century Schoolbook and Walbaum. Again, Geometric sans serifs marry best with these.
So what does all this actually look like in practice? Here's our a reference list of tried-and-testing font pairings that are guaranteed to avoid conflict.
01. Freight Sans and Freight Text

Freight is available in a range of weights and stylesAn example of a superfamily, GarageFonts' Freight is available in a large range of weights and styles, including Sans, Text, Display and Micro versions – giving you a versatile typographic toolkit.
02. Super Grotesk and Minion Pro

This match creates a luxurious finishThe ever-popular serifed Minion Pro works perfectly as a headlining font in this luxurious pairing. Coupled with the nimble sans-serif Super Grotesk, these two fonts carry a modern sense of elegance with minimal effort.
03. Kaufmann and NeutraDemi

At a dash of handwritten flair with this font pairingThe flowing, handwritten stylings of Kaufmann add a touch of personality to this odd couple. Offsetting the straight and angular sans-serifed NeutraDemi perfectly, these two might not make a likely match, but that doesn't stop them playing off one another beautifully.
04. Brandon Grotesque and Minion Pro

Minion Pro is the perfect choice for small textThe reliable Minion Pro makes another appearance, this time playing second fiddle to the bold and attention-grabbing Brandon Grotesque. It's a classic serif and sans-serif font pairing, with both typefaces remaining crisp and easy to scan.
05. Helvetica Neue and Garamond

A type match made in heavenA famously harmonious duo, with the ubiquitous Neo-Grotesque sans serif for headlines, and the classic Old Style serif for text. Mix up weights and sizes between the two neutral families to establish hierarchy.
06. Caslon and Myriad

1700s meets late 20th centuryAnother classic font pairing, this time between an 18th century Old Style serif and a late-20th century Humanist sans serif. Myriad is famously used in Apple's corporate communication, as well as in the Rolls Royce logo.
07. Fontin and Fontin Sans

These Dutch typefaces are ideal partnersOur second superfamily, Fontin was designed by Dutch foundry exljbris specifically to be used at small sizes, with a loose spacing and tall x-height. Fontin Sans is designed as an ideal partner for it.
08. Minion and Poppl-Laudatio

Two typefaces with personality that bond perfectlyAn Old Style serif typeface with personality, Minion was designed in 1990 but inspired by late Renaissance era type. Although technically a sans serif, Poppl-Laudatio's subtle flared details bring out its pronounced serifs.
09. Liberation Serif and Liberation Sans

An open source superfamily pairingAnother superfamily, which also includes Sans Narrow and Mono variations, Liberation was intended as an open-source substitute for many commonly used Windows fonts, such as Arial, Times New Roman and Courier New.
10. Trade Gothic Bold and Sabon

These readable typefaces combine wellThis pairing is particularly effective when Trade Gothic is used in its Bold weight for headlines, to set off Jan Tschichold's classic Old Style serif face for text. Both typefaces are highly readable, with a tall x-height, and combine well.
11. Scala and Scala Sans

A hugely versatile pairingFontFont's superfamily began with the serif version in 1990, followed in '92 by its sans serif companion. With small caps, various ligatures and old-style figures, it's hugely versatile and widely used in publishing.
12. Rockwell Bold and Bembo

Bold and attention-grabbing meets calmly neutralOne of the classic slab serifs, Rockwell was designed in the 1930s and has a huge amount of personality and attention-grabbing potential when used bold. The much more conservative serif Bembo is neutral but versatile.
13. Myriad Black and Minion

A great combination for clear hierarchyMyriad and Minion have already cropped up in different font pairings earlier in the list, but this combination of the shouty ultra-bold Black version of the former and the text weight of the latter achieves clear hierarchy.
14. Souvenir and Futura Bold

Two strong type personalities that work well togetherMixing two strong typographic personalities rarely works, as they end up fighting. Souvenir is softer and more playful than many of its Old Style serif counterparts, while Futura Bold is quirky without being too dominant.
15. Dax Bold and Caslon

Caslon's second entry on this listOne of the most versatile Old Style serifs, Caslon also appeared earlier on this list. Its neutrality lets the informal, modern Dax Bold deliver strong personality for a headline without competing for attention.
16. Aviano and Aviano Sans

Two tilting typefaces working in harmonyOnly available in all-caps varieties, Aviano has sharp, edgy serifs that give it a distinctive personality – while its sans serif version is smoother. They combine well to create hierarchy between two titling faces.
17. Antique Olive Bold and Chaparral

A quite distinctive font pairingInitially designed as an alternative to Helvetica and Univers, Antique Olive has a very tall x-height with short ascenders and descenders that make it highly distinctive in display form. Chaparral has a modern feeling but is a much more neutral slab serif.
18. TheSerif and TheSans

These typefaces were made to work togetherThe rather straightforward naming strategy within LucasFonts’ Thesis typeface superfamily makes the foundry's intentions pretty clear: these are totally complementary, and each comes with its own sub-varieties.
19. Renault Light and Apex-New

Contemporary sans serif meets authoritative serifAn ideal combination for formal corporate use: both Renault and Apex-New have a very similar ratio of x-height to body height for an effortless partnership between contemporary sans serif and authoritative serif.
20. Calluna and Calluna Sans

Calluna was born from experimentationAnother exljbris creation, Calluna was born out of an experiment with adding slab serifs to Museo, giving designer Jos Buivenga the idea of 'serifs with direction'. The result is a highly distinctive text face that later spawned a sans serif companion.
You might like these other typography articles:
View the full article