-
Content Count
454 -
Joined
-
Last visited
-
Days Won
76 -
Feedback
N/A
Posts posted by NickTheGreek
-
-
Welcome to Invision Community 4.3!
This release brings numerous improvements and several new features, so be sure to read our announcement for everything new!
Version 4.3.1 is a small maintenance update to fix issues reported since 4.3.0.
**IMPORTANT UPGRADE NOTICE**
Please note that not all third party applications and themes are yet compatible with Invision Community 4.3. If you utilize third party resources, including custom themes, please ensure they have been declared compatible by their respective authors or your site may be non-functional after upgrade. There is a new compatibility field on all marketplace resource listings. If this field is missing or does not specifically list 4.3, it is likely not yet compatible.Also included: 4.3.0
Welcome to Invision Community 4.3.0!
This release brings numerous improvements and several new features, so be sure to read our announcement for everything new!
**IMPORTANT UPGRADE NOTICE**
Please note that not all third party applications and themes are yet compatible with Invision Community 4.3. If you utilize third party resources, including custom themes, please ensure they have been declared compatible by their respective authors or your site may be non-functional after upgrade. There is a new compatibility field on all marketplace resource listings. If this field is missing or does not specifically list 4.3, it is likely not yet compatible. -

noticed this today
[Mon Apr 23 14:43:17.269029 2018] [ssl:error] [pid 26654:tid 140572910118656] AH01941: stapling_renew_response: responder error
[Mon Apr 23 14:43:32.308002 2018] [ssl:error] [pid 26035:tid 140572815709952] (70007)The timeout specified has expired: [client 94.66.43.86:39010] AH01974: could not connect to OCSP responder 'ocsp.comodoca.com'
[Mon Apr 23 14:43:32.308091 2018] [ssl:error] [pid 26035:tid 140572815709952] AH01941: stapling_renew_response: responder error
[Mon Apr 23 14:43:35.311210 2018] [ssl:error] [pid 27055:tid 140572773750528] (70007)The timeout specified has expired: [client 85.76.98.195:27343] AH01974: could not connect to OCSP responder 'ocsp.comodoca.com'and decided to look around
https://forums.cpanel.net/threads/any-problem-with-ocsp-comodoca-com-ssl.625667/
We are aware of the issue with Comodo as well and we're currently tracking it as part of an internal case CPANEL-19612. We'll update this thread with more information as soon as it becomes available
You can work around this issue by temporarily disabling SSL Stapling in Apache. This will cause client browsers to perform the OCSP check instead of waiting on your server to perform the check. The quickest way to do this is to:
1) Navigate to WHM -> Service Configuration -> Apache Configuration -> Include Editor.
2) Under "Pre Virtualhost Includes" set the drop-down to "All Versions"
3) In the text box, enter the following:
SSLUseStapling off
4) Click "Update" to save the changes, and then restart Apache.
=====
Alternatively, if you wish to do this via the command line, the following can be run:
For EA4:
== == == == == == == ==
echo "SSLUseStapling off" >> /etc/apache2/conf.d/includes/pre_virtualhost_global.conf; /scripts/restartsrv_httpd
== == == == == == == ==
For EA3:
== == == == == == == ==
echo "SSLUseStapling off" >> /usr/local/apache/conf/includes/pre_virtualhost_global.conf; /scripts/restartsrv_httpd
== == == == == == == ==
Once this issue has been resolved, we recommend removing this workaround.
Thank you,still looking for more resources
-
Invision Community 4.3
We are happy to announce the new Invision Community 4.3 is available!
Some highlights in Invision Community 4.3 include...
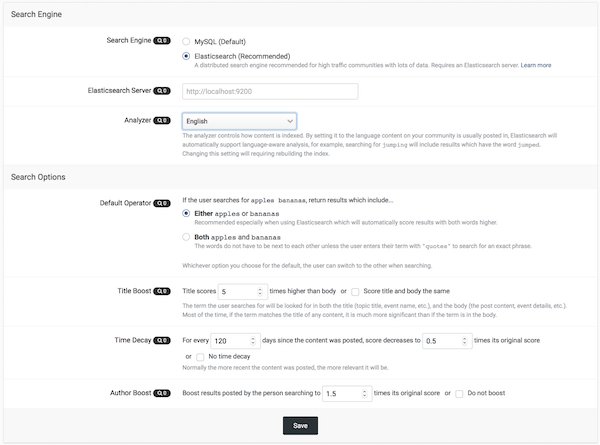
Improved Search
We now support Elasticsearch for scalable and accurate searching that MySQL alone cannot provided. There are also enhancements to the overall search interfaces based on your feedback.
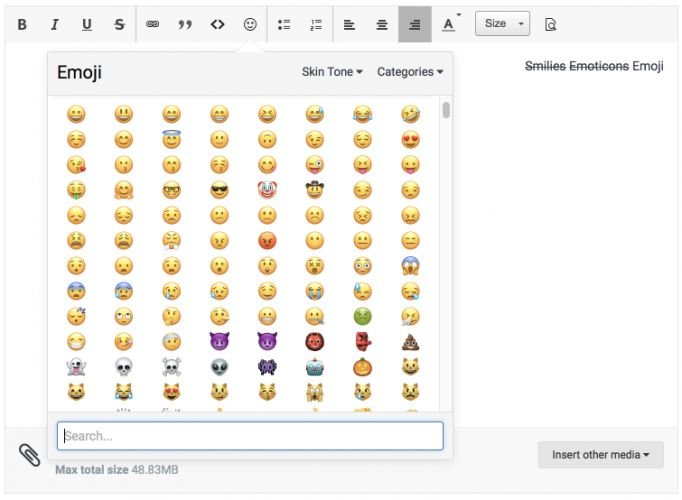
Express yourself with native emoji support in all editors. You can also keep your custom emoticons as you have now.
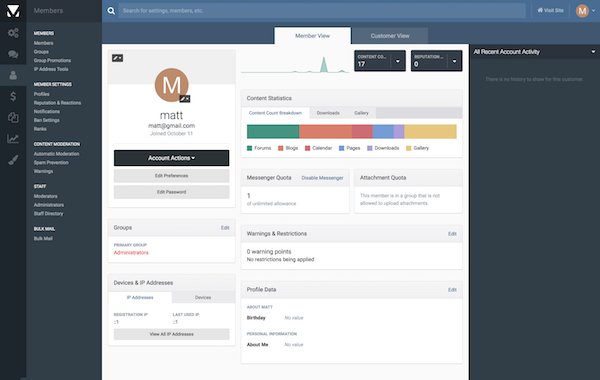
Member Management
The AdminCP interface to manage your members is all new allowing you easier control and management of your membership.
Automatic Community Moderation
You as the administrator set up rules to define how many unique member reports a piece of content needs to receive before it's automatically hidden from view and moderators notified.
The new Clubs feature has been a huge hit with Invision Community users and we are expanding it to include invite-only options, notifications, exposure on the main community pages, paid memberships, and more.
Custom Email Footers
Your community generates a lot of email and you can now include dynamic content in the footer to help drive engagement and content discovery.
We have reworked our Gallery system with a simplified upload process and more streamlined image viewing.
The full list follows. Enjoy!
Content Discovery
- We now support Elasticsearch which is a search utility that allows for much faster and more reliable searching.
- The REST API now supports search functions.
- Both MySQL and Elasticsearch have new settings for the admin to use to set search-defaults and default content weighting to better customize search logic to your community.
- Visitors can now search for Content Pages and Commerce Products.
- When entering a search term, members now see a more clear interface so they know what areas they are searching in and the method of search.
Member Engagement
- Commerce can now send a customizable account welcome email after checkout.
- You can whitelist emails in the spam service to stop false-positives.
- REST API has many enhancements to mange members.
- Ability to join any OAuth service for login management.
- Invision Community can now be an OAuth endpoint.
- Wordpress OAuth login method built in.
- Support for Google's Invisible ReCaptcha.
- Groups can be excluded from Leaderboard (such as admins or bot groups).
- All emails generated by Invision Community can now contain admin-defined extra promotional text in the footer such as recent topics, Our Picks, and more.
- Admins can now define the order of Complete Your Profile to better control user experience.
- Option to make a Club visible but invite-only
- Admins can set an option so any Club a member is part of will also show in the parent application. So if you are in a Club that has a Gallery tab then those image will show both in the Club and in the main Gallery section of the community.
- Club members can now follow an entire Club rather than just each content section.
- There is a new option on the Club directory page for a list view which is useful for communities with many Clubs.
- If you have Commerce you can now enable paid memberships to Clubs.
- Admins can set limits on number of Clubs per group.
- If a group has delete permission in their Club, they can now delete empty containers as well.
- Members can ignore invitations.
Moderation and Administration
- Unrestricted moderator or administrator permission sets in the AdminCP are visually flagged. This prevents administrator confusion when they cannot do something as they will be able to quickly see if their account has restrictions.
- You can choose to be notified with a new Club is created.
- Moderators can now reply to any content item with a hidden reply.
- Download screenshot/watermarks can now be rebuilt if you change settings.
- Support for Facebook Pixel to easily track visitors.
- Moderators can now delete Gallery albums.
- Automatic moderation tools with rules to define when content should auto-hide based on user reports.
- Totally new member management view in AdminCP.
- More areas are mass-selectable like comments and AdminCP functions for easier management.
New Features
- Commerce now has full Stripe support including fraud tools, Apple Pay, and other Stripe features.
- Commerce packages can now have various custom email events configured (expiring soon, purchased, expired).
- Full Emojii support in the editor.
- Setting so when someone is typing in an editor, other members will see a "Member X is typing..." status in the editor view.
- Complete overhaul of the Gallery upload and image views.
- Announcements system overhaul. Now global on all pages (not via widget) and new modes including dismissible announcements and top-header floating bar option.
- Many new reports on traffic and engagement in the AdminCP.
- Blog has new view modes to offer options for a traditional site blog or a community multi-member blog platform.
- The content-starter can now leave one reply to Reviews on their item.
- Commerce now makes it much easier to do basic account-subscriptions when there is no product attached.
Useful Improvements
- Forums has a new widget where you can filter by tags.
- If tags are not required, the tag input box now indicates this so the member knows they do not have to put in tags.
- Member cover photos can now be clicked to see the full image.
- Any item with a poll now has a symbol on the list view.
- Twitch.tv embed support.
- You can now update/overwrite media in the Pages Media Manager.
- Mapbox as an additional map provider to Google Maps.
Technical Changes
- Direct support for Sparkpost has been removed. Anyone currently using Sparkpost will automatically have their settings converted to the Sparkpost SMTP mode so your email will still work.
- Your cache engines (like Redis) will be checked on upgrade and in the support tool to ensure they are reachable.
- Third-party applications will now be visually labeled to distinguish them from Invision Community official applications.
- The queued tasks list in the AdminCP is now collapsed by default as queued tasks are not something people need to pay much attention to during normal operations.
- When upgrading from version 3 series you must convert your database to UTF8 and the system saves your original data in tables prefixed with orig. The AdminCP now alerts you these are still present and allows you to remove them to reclaim storage space.
- On new installs there are now reasonable defaults for upload limits to keep people from eating up storage space.
- Categories in all apps (forums, gallery albums, databases, etc.) no longer allow HTML in their titles. This has been a concern both in terms of security and usability so we were forced to restrict it.
- Large improvements to the Redis cache engine including use for sessions.
- The login with HTTPS option has been removed and those who were using it will be given instructions to convert their entire community to HTTPS.
- Images loaded through the proxy system now honor image limits for normal uploads.
- We now consider BBCode deprecated. We are not removing support but will not fix any future issues that may come up.
There's a lot to talk about here so we are going to lock this entry to comments so things do not get confusing. Feel free to comment on upcoming feature-specific entries or start a topic in our Feedback forum.
-
IPS Community Suite 4.3.0
Released 04/17/2018
Key Changes
Welcome to Invision Community 4.3.0!
There is a lot to know so be sure to read our announcement for everything new!
-
IPS Community Suite 4.2.9
Released 04/18/2018
This is a security release and we recommend all clients upgrade as soon as possible.
Key Changes
This is a maintenance to release to the 4.2 series address security issues.
As we prepare for our next large release, version 4.3, we do large security audits. We decided to apply those security enhancements to the 4.2 series so you can get them now if you prefer to not upgrade to 4.3 yet.
We would like to thank @newbie LAC for his assistance.
-
κάτι ήξερα ισως και εκοβα ακομη και την 8083 by default. μεχρι τώρα δεν εχω βρει κάτι κάπου
-
 1
1
-
-
εχω δεί τόσα vesta να σπάνε on update που να δείς οτι ίσως λύσει το θέμα και δημιουργήσει άλλα

-
alarming, to say the least
-

31st of March is World Backup Day, a global initiative that aims to get organisations and individuals to pledge to back up their data on that day. As a web host, it’s something we fully support and we’ve written this article to explain why you should join in. To give you a little more incentive, we’ve also got a couple of superb backup deals on offer which we’ll tell you about at the end of the post.
If you’re one of our regular readers, you’ll know that this is not the first post we’ve written about backups – and it’s unlikely to be the last. Backing up is one of the things that people need to be constantly reminded to do. Most of us know why we should but, for some reason, we don’t always see it as a priority. Data loss is what happens to others – isn’t it?
If you aren’t overly concerned about the need to backup your data, here are a few points to get you thinking.
Malware vulnerability
According to Sophos, over 300 million new pieces of malware are created to infect websites and computers every year. This results in 10% of all computers being infected every month and 30,000 websites being infected every single day. When viruses infect, data is lost and software is corrupted.
And these infections can spread beyond just computers and websites. Viruses can be transmitted to phones, tablets, pen drives, camera cards and other storage devices – and done so unwittingly by employees and customers.
Whilst antivirus software can usually protect you, the companies that make the software have to detect the malware first and then discover a way to eradicate it. Unfortunately, you can’t detect malware until it is already out there doing damage in the first place.
Having a clean backup means your data isn’t lost and your business recovers far quicker and with significantly less expense.
Hacking

Surprisingly, most website owners think hacking is a conscious undertaking done by an individual who chooses a company to target. This leaves them to believe that no-one would be interested in hacking their organisation and so they have little to fear. “We’re a plumbers’ merchant in Hampstead Heath, nobody would want to hack us.”
It doesn’t quite work like that.
Hacking is very much an automated process where computer programs, not too dissimilar to Google’s search bots, scour the entire internet looking for sites which have vulnerabilities. It is these sites which are then targeted; and the actual break in is much more likely to be done using highly sophisticated software rather than by some hooded character, wearing a Salvador Dali mask, beavering away at a keyboard.
Anyone who has any kind of hacking detection software, such as the WordPress Wordfence plugin, will know that even small websites have multiple attempted break-ins on a daily basis. Indeed, 66% of all attacks are on SME’s and in 2016 there is expected to be a 37% increase in the number of attacks.
Whilst one of the biggest threats of hacking is that data will be stolen, there is also the risk of data being lost. Once an intruder has access to your admin panel, there is nothing they cannot do. If they wish, they can delete everything and take down your entire system.
I put it somewhere….
Human error is one of the most significant causes of data loss for businesses. Hundreds of thousands of computers and phones go missing every year. Even back in 2008, a study found that 12,000 laptops were lost every week, just in US airports. If you are a small business and you keep your entire business records on your laptop, losing it can have enormous consequences: invoices, clients’ work, contact details, emails, website content, account details, logins, portfolios… all of it important information. It’s not just a matter of it potentially being stolen or accessed, if it is not backed up, it’s gone.
It’s not just misplacing hardware where human error causes problems; we erroneously delete data and carelessly break our devices.
There are 84,900,000 results on Google for the term ‘phone down the toilet’ and over 25 million for ‘spill water on computer’ which indicates how many people have put their data in jeopardy just by accident. And, of course, devices are prone to breaking down and hard drives to failing.
A regular backup would ensure that when your device dies, the data will live on and your organisation can make a full recovery.
Make your World Backup Day pledge
We’d like to think that we’ve done our bit here to remind you just how important backing up your data can be and hopefully this will encourage you to support World Backup Day on 31st March by pledging to backup on that day. You can find out more about World Backup Day by watching the video below.
Need an incentive? Here are our offers
Hopefully, we’ve convinced you that regularly backing up your data is absolutely essential. To make things easier we have got two offers which you might be interested in.
Firstly, if you buy any of our VPS, Cloud or Dedicated server packages on World Backup Day, 31st March, well give you a 25GB of backup storage, FREE for 12 months. If you don’t need a VPS, Cloud or Dedicated server package but still want a backup facility, we’re offering 25% off any backup purchased on 29th, 30th, 31st March.
-
 1
1
-
-
I am using rsync to recursively sync a remote folder tree that looks something like the following:
/folderA/a1/cache /folderA/a1/cache/A1 /folderA/a1/cache/A2 /folderA/a1/somefolder /folderA/a1/someotherfolder /folderA/a2/somefolder/cache /folderB/cache/ /folderB/b1/somefolder/cache /folderB/b1/somefolder/yetanotherfolder/cache /folderB/b1/somefolder/yetanotherfolder/cache/B1 /folderB/b1/somefolder/yetanotherfolder/cache/B2I don't know what the folder tree will look like and it will change over time. So what I want to be able to do is recursively rsync the above but exclude the folder "cache" and any sub folders it contains so that I ultimately end up syncing:
/folderA/a1 /folderA/a1/somefolder /folderA/a1/someotherfolder /folderA/a2/somefolder /folderB/ /folderB/b1/somefolder /folderB/b1/somefolder/yetanotherfolder/Any suggestions?
>>
You want the
--excludeflag. For example, a local rsync:rsync -a --exclude cache/ src_folder/ target_folder/-
 1
1
-
-
-
-
It is very easy. The solution is on nixCraft, but on the comments.
## 64 bit linux ## wget https://www.rarlab.com/rar/rarlinux-x64-5.5.0.tar.gz tar -zxvf rarlinux-x64-5.5.0.tar.gz cd rar sudo cp -v rar unrar /usr/local/bin/
There’s no need to compile or anything. The binary on the tar file works out of the box. On the above example, we copy it on /usr/local/bin so it is found by default after login on our system. Other “exotic” solutions are possible, but I don’t want to make suggestions.
https://bitsanddragons.wordpress.com/2018/01/09/install-rar-unrar-on-centos-7/
-
 1
1
-
-

Rest In Peace, Professor
-
always useful
-
-
-
-
this one is ready
Your Invision Community 4 is ready
The upgrade process is now complete and your Invision Community is now ready!
-
underway, i have to also cover a glitch with their system while trying to pay for license
"Sorry, there is a problem
The page you are trying to access is not available for your account.
Error code: 2X196/1"
opened a ticket with them
-
Changing the Postfix maximum email size
I've recently had some of my customers emailing me large image attachments and my Postfix mail server has been rejecting them. A quick look at the postfix configuration showed the message size limit was the default so I needed to increase it. This post looks at how to see what the current email message size limit is with Postfix and how to change it.
The configuration option is "message_size_limit" and by default is set to 10240000 bytes which is roughly 10MB. You can see what setting your postfix install is currently using by issuing the following command:
postconf | grep message_size_limit
Just doing "postconf" on its own will show all the options so using grep on "message_size_limit" filters the output to just the setting we want. For the default setting, you'll see this:
message_size_limit = 10240000
To change the setting to some other value, open the main.cf file in your favourite text editor (it's often at a location like /etc/postfix/main.cf) and either edit or add the following line, depending if it's already in the file or not.
message_size_limit = 20480000
In the above example I've changed it to ~20MB.
Then reload postfix like so:
service postfix reload
and your setting will take effect. You can query postconf again if you want to check all is as expected.
https://www.electrictoolbox.com/postfix-email-size-limit/
-
$ echo -en "\x00\x00\x00\x00\x00\x01\x00\x00stats\r\n" | nc -q1 -u 127.0.0.1 11211
If you see non-empty response, your server is vulnerable.
-
-
The Israeli security researcher Barak Tawily a vulnerability tracked as CVE-2018-6389 that could be exploited to trigger DoS condition of WordPress websites.
The expert explained that the CVE-2018-6389 flaw is an application-level DoS issued that affects the WordPress CMS and that could be exploited by an attacker even without a massive amount of malicious traffic.
“In this article I am going to explain how Denial of Service can easily be caused to almost any WordPress website online, and how you can patch your WordPress website in order to avoid this vulnerability being exploited.” reads the analysis of the expert.
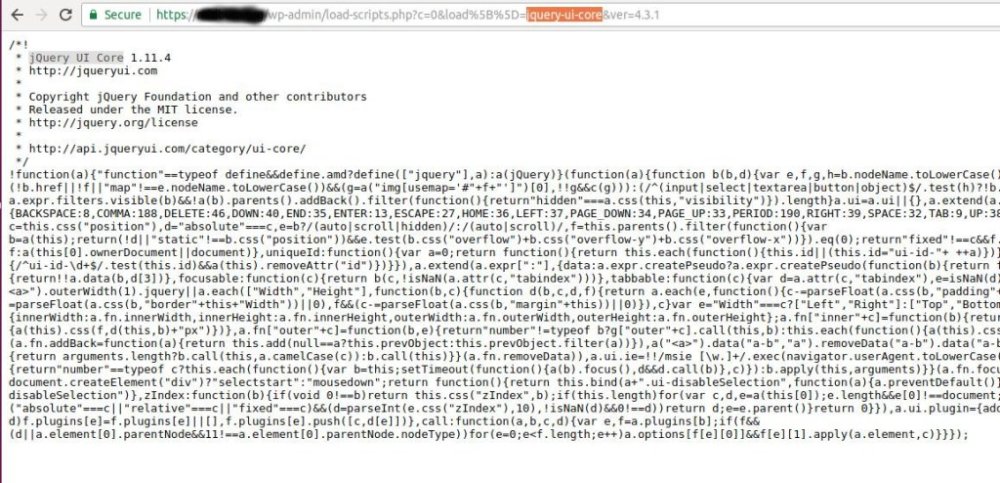
Tawily revealed that the flaw exists in almost all versions of WordPress released in last nine years, including the latest one (Version 4.9.2).The flaw affects the “load-scripts.php” WordPress script, it receives a parameter called load[] with value is ‘jquery-ui-core’. In the response, the CMS provides the JS module ‘jQuery UI Core’ that was requested.
As you know, WordPress is open-source project, for this reason, it was easy for the expert to perform code review and analyzed the feature in detail.
The load-scripts.php file was designed for WordPress admins and allows to load multiple JavaScript files into a single request, but the researcher noticed that that is is possible to call the function before login allowing anyone to invoke it.
The response provided by the WordPress CMS depends upon the installed plugins and modules. It is possible to load them by simply passing the module and plugin names, separated by a comma, to the load-scripts.php file through the “load” parameter.The ‘load-scripts.php’ finds the JavaScript files included in the URL and appends their content into a single file and then send back it to the user’s web browser.
The researcher highlighted that the wp_scripts list is hard-coded and is defined in the script-loader.php file, so he decided to send a request that in response will get all the JS module of the WordPress instance.
“There is a well-defined list ($wp_scripts), that can be requested by users as part of the load[] parameter. If the requested value exists, the server will perform an I/O read action for a well-defined path associated with the supplied value from the user.”
“I wondered what would happen if I sent the server a request to supply me every JS module that it stored? A single request would cause the server to perform 181 I/O actions and provide the file contents in the response.”
Tawily developed a proof-of-concept (PoC) python script called doser.py that he used to makes large numbers of concurrent requests to the same URL to saturate the resources of the servers.
An attacker with a good bandwidth or a limited number of bots can trigger the CVE-2018-6389 vulnerability to target popular WordPress websites.
Tawily reported this DoS vulnerability to the WordPress team through HackerOne platform, but the company refused to acknowledge the flaw.
“After going back and forth about it a few times and my trying to explain and provide a PoC, they refused to acknowledge it and claimed that:
“This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress’s control.“” Tawily wrote.The expert has implemented the mitigation against this vulnerability in a forked version of WordPress, he has also released a bash script that addresses the issue.
https://securityaffairs.co/wordpress/68709/hacking/cve-2018-6389-wordpress-dos-flaw.html







Spam Prevention
in Invision forum
Posted · Report reply
Spam Prevention
People signing up on your community just to post spam is a never ending battle much like spam in your email inbox. IPS Community Suite has tools to help you fight that battle.
CAPTCHA
In the captcha section you will be able to choose a captcha type. These prevent automated spam bots by asking the user to enter text shown, complete a puzzle, or an automatic detection to prove that a user is human.
Invision Community 4.2 and below support reCAPTCHA, reCAPTCHA 2 and keyCAPTCHA.
Important Note: Google has discontinued reCAPTCHA v1 and this service is no longer available. If you are using Invision Community 4.2 or below, you will need to reset your CAPTCHA service preference to reCAPTCHA 2 or keyCAPTCHA. Be aware that both services will require you to register for a (free) API key before you can use them. Links to sign up for a free API key are available in the AdminCP on the CAPTCHA configuration page.
Invision Community 4.3 and above support reCAPTCHA 2, keyCAPTCHA and Invisible reCAPTCHA.
Flagging Spammers
The "Flagging Spammers" section is where you can set up what happens when a member on your community is flagged as a spammer. This will allow you to have a member automatically banned, remove submitted content and notify someone if you wish to do so.
IPS Spam Service
The IPS Spam service is a free service provided by IPS to clients with an active licence. From here you can set up what automatically happens to these users when they are detected as being a potential spammer by the service.
Question and Answer Challenge
The question and answer challenge gives you an extra customisable set of questions and answers you can present to a potential member to ensure that the user is human and not an automated spamming bot. You can put whatever questions you like in here for people to answer along with multiple possible answers.